In this article we will see how zPhisher works and we will demonstrate the procedure how the attack occurs. Zphisher is one of the most powerful and open-source automated phishing tools. It is the upgraded version of Shellphish. Zphisher automates the process of Phishing and makes it way easier than previously developed phishing tools.
What is a Phishing attack ?
Phishing attacks is the most and widely used social engineering attack mainly through an email that consists of a malicious link . Hackers often use this type of attack to steal sensitive information like login credentials and credit card numbers. The stolen social media credentials are later used to lure and steal money and other valuables from unsuspecting social media users, friends and family. Phishing is often used to gain a foothold in corporate or governmental networks as a part of a larger attack, such as an advanced persistent threat (APT) event.

Zphisher - Automated Phishing Tool for Social Media Accounts Hacking
Also Read: BeEF - Browser Exploitation Framework [Ethical Hacking Tutorial]
Before moving on further, let's see how to install Zphisher on Linux using below Installation Guide.
NOTE:
Installation Guide
There are multiple ways to install Zphisher on a Linux System but here we will discuss two of the most famous ways. You can use any of the below methods depending on your choice.
a) Using GitHub
The first step is to open the git repository https://github.com/htr-tech/zphisher and copy the link.
After copying the link the Second step is to open our linux terminal and run the following command to clone the source code into our local machine.
>>> git clone https://github.com/htr-tech/zphisher
The third step will be opening the directory and inside we will get these files.
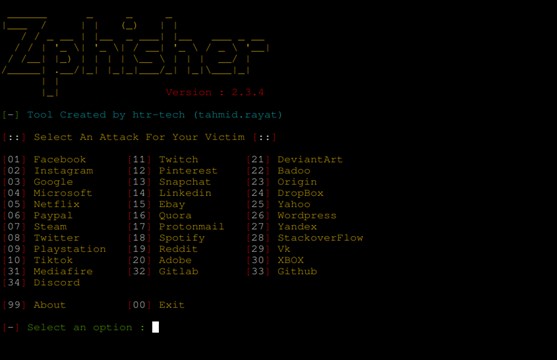
The final step will be running the zPhisher Script with the command specified below and we are up and running
>>> bash zphisher.sh
b) Using Docker
To install zPhishing using docker we pull the repository from the DockerHub.
>>> docker pull htrtech/zphisher
And to start the container we will use the following command:-
>>> docker run --rm -ti htrtech/zphisher
Or simply we will use the wrapper script run-docker.sh using the command:-
>>> curl -LO https://raw.githubusercontent.com/htr-tech/zphisher/master/run-docker.sh
>>> bash run-docker.sh
Usage
Zphisher is a tool developed by hr-tech to be used for advanced social media credentials phishing. The tool is an improvement of another tool, shellphish. The difference between zphisher and shellphish is that zphisher has updated templates for different social media platforms. Zphisher also allows port forwarding using Ngrok.
Important Features
- Mask URL support.
- It is written in Bash language
- It has the latest login pages.
- It is very simple and easy to use.
- It has multiple tunneling options like Ngrok,, LocalHost, LocalXpose and Cloudflare.
- Easy to use and User-friendly tool.
- Docker support.
How Phishing Works
Once we are done with setting up our Environment for the zPhisher our next move will be to demonstrate how the Phishing process works using zPhisher. zPhisher has over 30 fake web pages that we can use. We just have to select in our best interest that could lead to an effective hack. So our Next move will be to select one of the available web platforms as shown in the figure.
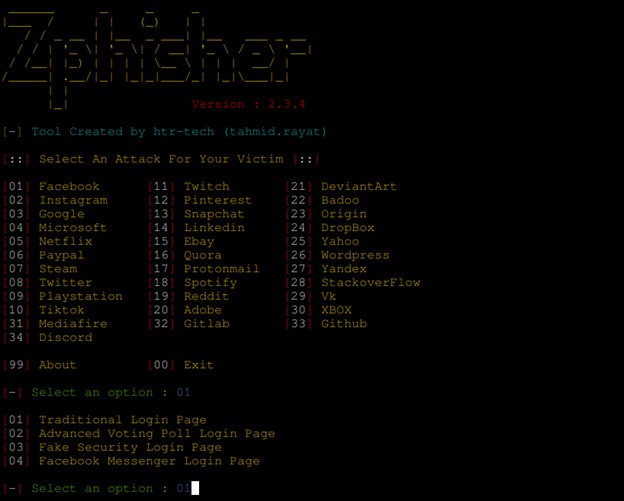
For example if we want zPhisher to generate a fake facebook web platform we simply write “01” and hit “Enter”. After selecting the web platform then we will have an alternative to choose a specific web page that zPhisher can offer us. And again let’s say we have selected the “Traditional Login Page” option.
The next step is going to be Port Forwarding. Port forwarding, sometimes called port mapping, allows computers or services in private networks to connect over the internet with other public or private computers or services.
Port forwarding achieves by creating an association called a map between a router’s public, wide area network (WAN) internet protocol (IP) address and a private, local area network (LAN) IP address for device on that private network.
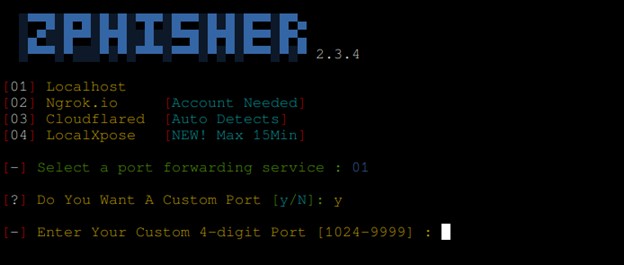
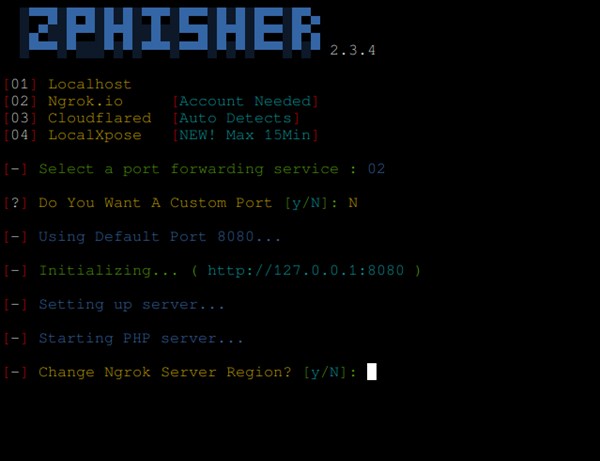
In zPhisher we have 4 kinds of port Forwarding techniques. For example, like the above figure, if we want to launch the fake web page and access it on our local machine we will select the option “Localhost” which is 01 and we can input a specific port that service should be running or zPhisher has an option to assign default port. After filling the port forwarding technique and port the server should be up and running.
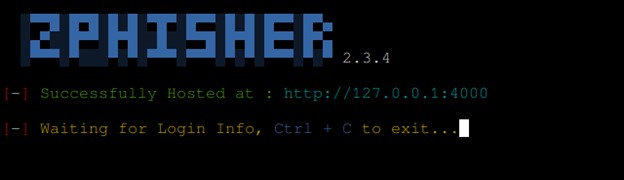
The Next step is to open our browser and paste the link http://127.0.0.1:4000
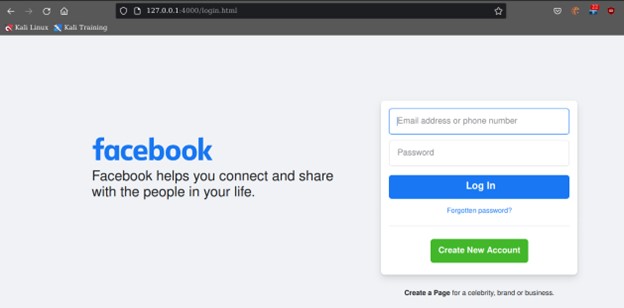
The above picture shows a fake page generated by zphisher and served in localhost. It looks like the real facebook page but when we start to enter our login credentials it automatically transfers it to the server we initiated and redirects to the real facebook page.
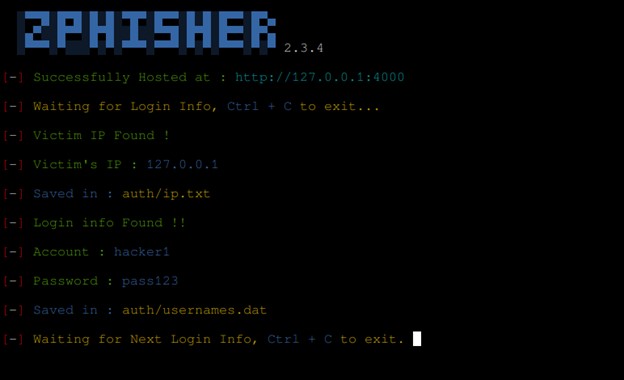
As the image shows, the server has now captured the login credentials and saves it to a file called “usernames.dat” in the directory “auth”. One of the main features that zphisher possesses is that it has Ngrok, cloudflare and Localxpose integrated to it which we can use very easily.
If we want to execute a phishing attack on a remote machine we would have to use one of the port forwarding tools listed below in the picture.
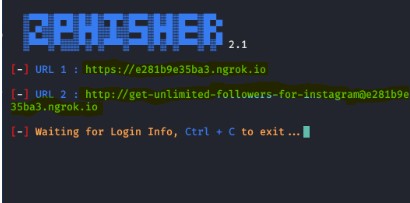
By selecting on of the port forwarding method we will have a generated link that we can use outside our network
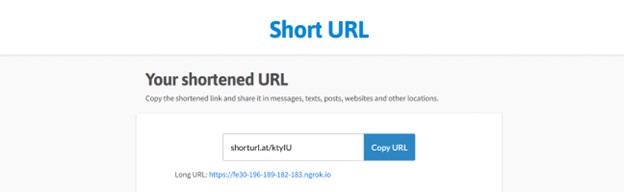
The other thing is we can shorten our link in order to trick our victim. To do that we just have to go to https://www.shorturl.at/ and paste our long url to the form and we have our shortened link that we can use on our target.
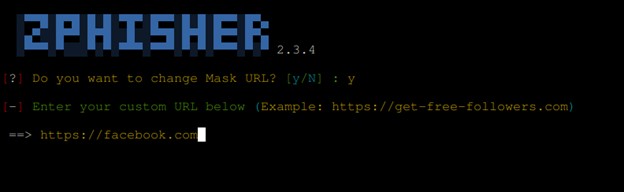
zPhisher has also the feature of Masking a url. A Masked URL empowers attackers to use content from another domain while keeping your original domain name in the address bar. This feature helps hackers to change a complex url generated by the port forwarding to a more known url that can trick victims on clicking the link.
Conclusion
Nowadays attackers, especially hacktivists, are turning their face to social media and big corporations. And in order to hack into these platforms hackers mostly use Social Engineering techniques mostly Phishing because human beings are the weakest link so far and most hacking is executed through employers without their knowledge.
In order to execute Phishing attacks, zPhisher has been the most widely used Phishing tool. It is one of the most easier, efficient and powerful phishing tools for quite some time. Since zPhisher has already built in fake web pages and integrated port forwarding tools that provides with domain name which enables attacker to send their malicious link into remote machine
