In this article we will see how to use Hashview front end for cracking hashes but before that let's first understand what is Hashing ? It is the process of converting a given key into another value. A hash function is used to generate the new value according to a mathematical algorithm. The result of a hash function is known as a hash value or simply, a hash. Ethical hackers and Cyber analysts use different kinds of tools, one of which is HASHVIEW. More on official website.
![Using HashView Front end for Password Cracking [Ethical Hacking]](https://www.socialyzehub.com/wp-content/uploads/2022/12/hashv.jpg)
Using HashView Front end for Password Cracking [Ethical Hacking]
Also Read: Introduction to Cross Site Request Forgery(CSRF) | Ethical Hacking
Hashview is a web based platform that helps organize and automate repetitive tasks related to password cracking. Hashview uses the hashcat command in a simpler web based manner. The tool is broken into two components - server and client. The Hashview server is the system deployed on hardware to give access to breaking hash value for the hashview clients. But both the component can be deployed and used in one device.
Hashview executes the hashcat command to decode hash values given as an input in the web application. This is a password-cracking tool that can be used in cracking the hash of some of the most complex password formats. It provides adaptability, effectiveness, and many ways to decipher a given passphrase in order to do that. When efficiently cracking hashes, Hashcat also enables the usage of already created dictionaries, brute force, and even rainbow table approaches.
Features of Hashview
a) Multi User Support
Hashview supports multiple users as a client that is deployed on one server. Each User can create an account and use Hashview. Hashview has also provided users to use the system individually as well as in a group. While using a Group team members can know who is cracking what kind of hash hence, they can share a decoded value.
b) HashCat Control
Hashview provides users to use a hashcat command in a simple and understandable user interface. It also allows control of the most commonly used switches.
c) Analytics
Analytics is the most significant feature of the tool Hashview. Most Ethical Hackers needs to submit a report about their findings and this feature automates the generation of a report. Hashview can generate a detailed report.
d) Job Queuing
Users can Queue jobs so that they can increase the duty cycle of cracking passwords. It also supports multiple threads when cracking hashes. Multiple threads will make the process of hash cracking much faster. And Those Threads can be configured and executed based on priority.
e) Better Performance
Performance and optimization-focused implementations of more than 90 algorithms are possible. Sessions can be stopped and automatically restored. At startup, they distinguish retrieved hashes from the output file. They can also decode both types of hex (hex-charset and hex-salt).
Other Features
- Hashview stores already cracked hashes and enables users to use already those hashes at any time.
- Notifies the user after completion of a process hash cracking.
- Hashview supports multiple hashing algorithms.
NOTE:
Installation
Installing Hashview is a little bit tricky but we will see it step by step. First you need to have below prerequisites in place:-
- mysql server
- python3 -flask
Then next step is to install mysql-server but before that we need to update our apt repository using below command.
$ sudo apt update
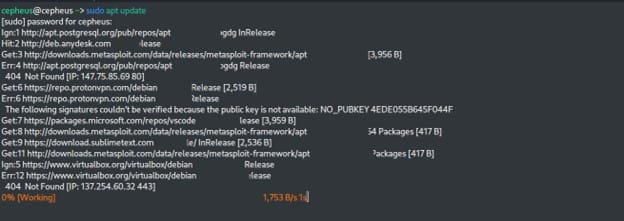
Our next task will be to install a mysql server on our machine. The MySQL server provides a database management system with querying and connectivity capabilities, as well as the ability to have excellent data structure and integration with many different platforms. We use the following command to install mysql-server on our machine.
$ sudo apt install mysql-server #on Ubuntu Machine
$ sudo apt install default-mysql-server #on Kali Machine
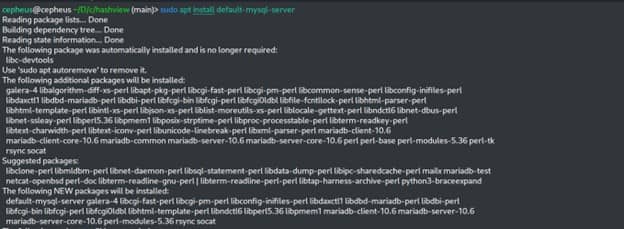
After the installation is completed, we will then configure our mysql database by creating an account, a user and a table for our hashview tool. To configure our mysql database, we need to first initiate our service with the below command.
$ sudo service mysql start #to initiate
$ sudo service mysql status #to see the Status
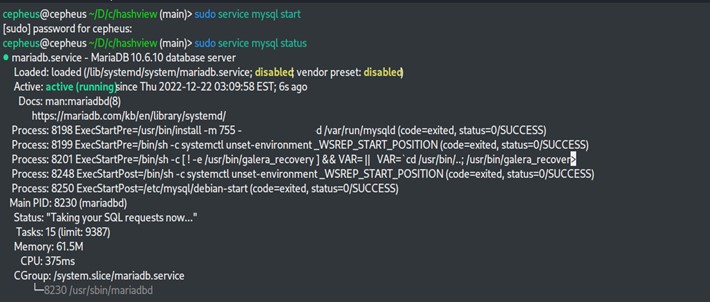
Then we need to run mysql_secure_installation to improve the security of mysql server. You will be asked to enter root password and few other queries as shown below.
$ sudo mysql_secure_installation
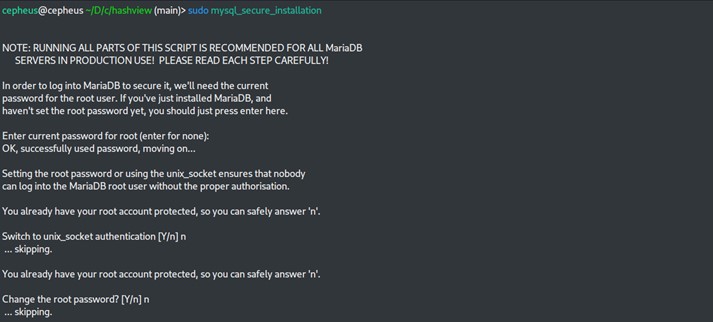
After setting up the security, we will then create a user in the database and grant full privileges on hashview . To start the process we will run below command.
# to start the process
$ sudo mysql
# to create a database
$ create database hashview;
# to create a user
$ CREATE USER 'yourusername'@'localhost' IDENTIFIED BY 'YOURPASSWORD!';
# to grant a privilege for the user
$ GRANT ALL PRIVILEGES ON hashview.* TO 'hashview'@'localhost';
$ FLUSH PRIVILEGES;
#to exit
$ exit;
Now that our database is configured, it can store our hash values and account information. After Installing and configuring our mysql database we will then install Hashcat. It is a popular and effective password cracker widely used by both penetration testers and sysadmins as well as criminals and spies. To install hashcat we will use the following command.
$ sudo apt install hashcat
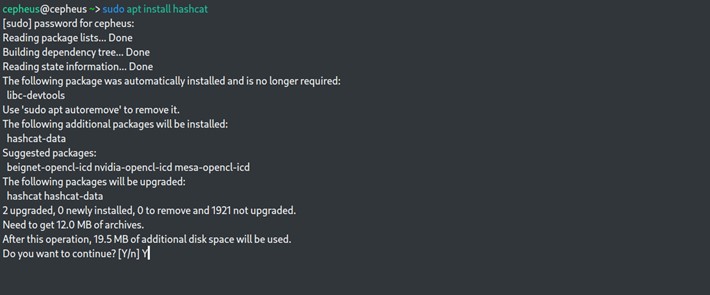
Now we will install a hashview server on our machine. To do that we will go to github.com and clone our source code using below command.
$ git clone https://github.com/hashview/hashview.git
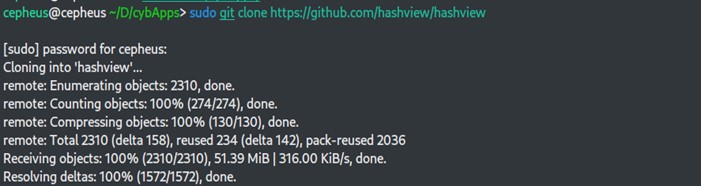
After cloning our hashview source code we need to install dependencies on our machine with the below command.
$ pip3 install -r requirements.txt
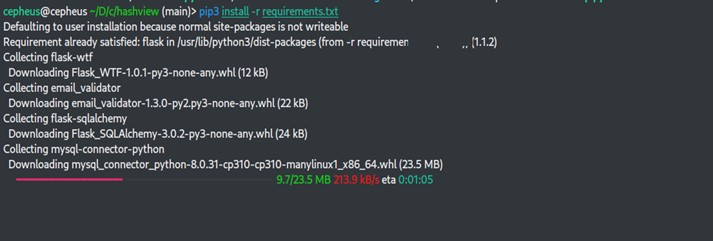
After installing the requirement, our next task will be to set up hashview with the below command.
$./setup.py
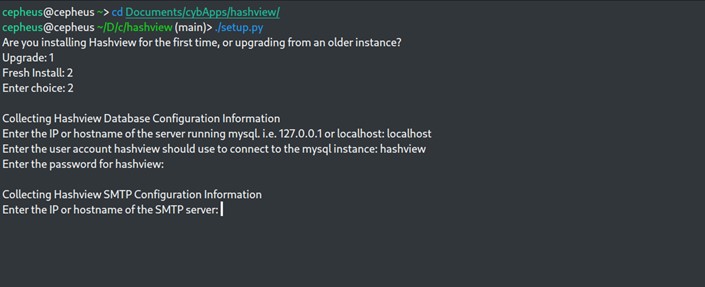
While setting up hashview we will be prompted with different kinds of forms which we need to fill carefully. Now we can start our hashview server by running below python script.
$ python3 hashview.py
Then we need to open our browser and enter the url http://0.0.0.0:8443 as shown below.
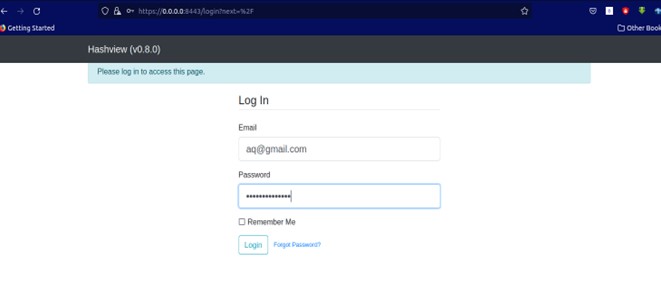
Here we will install a Hashview-agent that enables us to crack hashes. To install hashview-agent we need to download it by redirecting to http://localhost:8443/agents and download as shown below.
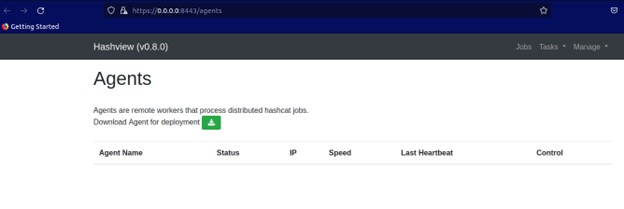
After downloading the file, we need to uncompress it using below tar command:-
$ tar -xzvf hashview-agent.0.8.0.tgz
Then install all the dependencies using below command:-
$ pip3 install -r requirements.txt
Finally start the hashview-agent using the given below command
$ python3 hashview-agent.py
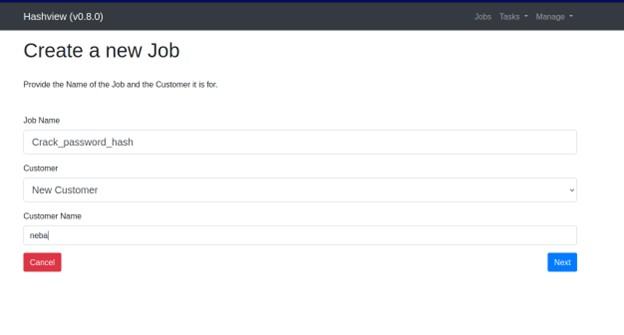
Now we are done installing hashview let’s get cracking hashes to do that we need to assign Jobs. After providing the job details below, click on Next to proceed.
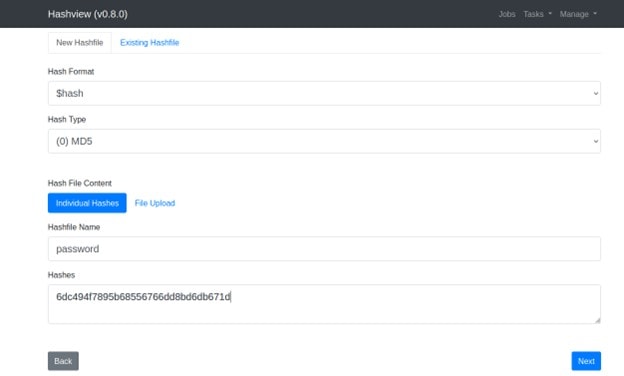
Here you need to provide the Hashes and then click on Next.
You can also set the notifications option from here and then click on Next.
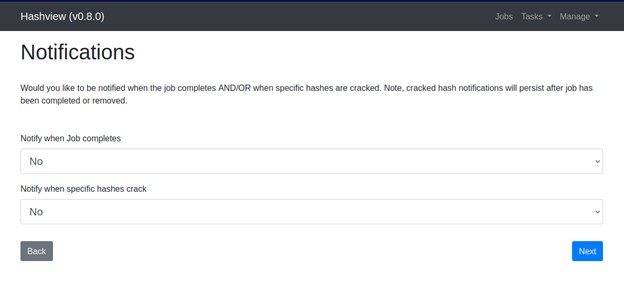
Finally you need to set the wordlist(this could be different for you) task that will be assigned to the Job as shown below.
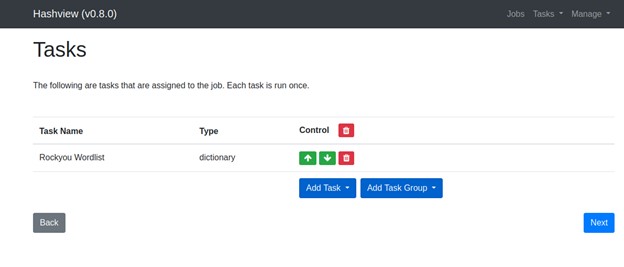
By going to the Jobs page after the agent has been granted permission, we can now create a job. We must enter details while creating a job on hashview, including the hash file from which we are decrypting the hashes, the job's name, the client, and the world list file to use for that task. Once everything is set up, we can begin working quickly. By specifying to receive email notifications when a hash has been broken, we may use hashview to execute unattended cracking.
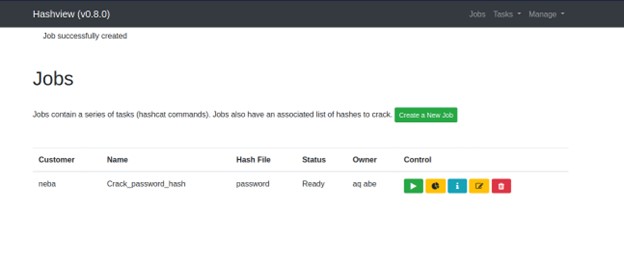
Conclusion
So far we have seen about Hashview and Hashcat tools that can automates cracking of hashes. And hashview is one of the best simple and easy to use cracking tools. The success of cracking hashes mainly depends upon the performance of the hardware where the tool is installed because cracking mainly depends on trying every possible outcome.
