John The Ripper is an open source Password cracking tool used for various multipurpose reasons. This tool consists of different modules and programs that are tasked with different purposes. It supports several common encryption technologies out-of-the-box for UNIX and Windows-based systems. This tool detects a password strength that could put a system at risk. John the Ripper not only cracks passwords, they are also used to identify crypto hashes that are found on several devices.
John The Ripper - Password Cracking Tool [Ethical Hacking]
Also Read: ThePhish: Learn about an Automated Phishing Email Analysis Tool
John The Ripper auto detects the encryption on the hashed data and compares it against a large plain-text file that contains popular passwords, hashing each password, and then stopping it when it finds a match.
Here is the list of encryption technologies found in John the Ripper:-
- Unix crypt(3)
- Traditional DES-based
- “bigcrypt”
- BSDI extended DES-based
- FreeBSD MD5-based (linux and Cisco IOS)
- OpenBSD Blowfish-based
- Kerberos/AFS
- Windows LM (DES-based)
- DES-based tripcodes
- SHA-crypt hashes (newer versions of Fedora and Ubuntu)
- SHA-crypt and SUNMD5 hashes (Solaris)
NOTE:
Installation
Users can install John The Ripper through many ways. On the common linux OS, we can use the apt and snap repository.
>> sudo apt install john #or
>> sudo snap install john-the-ripper
Ways to Crack a Password
Hackers and Cryptanalysts use different kinds of ways to crack a password or hash file that can be found in different devices and systems, most of which is Brute forcing.
There are mainly three types of password cracking:-
a) Dictionary Attacks : The perpetrators attempt to break the encryption or gain access by spraying a library of terms or other values. The data used for automated insertion into the target can be words in a dictionary or number sequences, however it is growing more common for data in a dictionary attack to be less random.
An attacker tries each of the words in a dictionary as passwords to gain access to the system via some user's account. If the password chosen by the user was a word within the dictionary, this attack will be successful (in the absence of other mitigations).
b) Brute Forcing : Attacks accounted for five percent of confirmed security breaches. An adversary tries every possible value for a password until they succeed. A brute force attack, if feasible computationally, will always be successful because it will essentially go through all possible passwords given the alphabet used (lower case letters, upper case letters, numbers, symbols, etc.) and the maximum length of the password.
A brute force attack involves ‘guessing’ username and passwords to gain unauthorized access to a system. Brute force is a simple attack method and has a high success rate.
c) Rainbow attack : Rainbow tables are precomputed tables to revert hash codes to the original input plaintext. In short, these tables keep the original input plaintext associated with the corresponding hash code after some operations of hashing and reduction.
It is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored in a database system. A rainbow table works by doing a cryptanalysis very quickly and effectively.
A rainbow table is a hash function used in cryptography for storing important data such as passwords in a database. Sensitive data are hashed twice (or more times) with the same or with different keys in order to avoid rainbow table attacks. A rainbow table works by doing a cryptanalysis very quickly and effectively.
How does John The Ripper work ?
By default John tries “single” then “wordlist” and finally “incremental”. Modes can be understood as a method John uses to crack passwords.
- Single crack mode : This mode is the faster technique to crack a password in a machine. This mode uses information from UNIX passwd files users' full names, usernames, etc. as present in GECOS fields within UNIX passwd/shadow files to “guess” passwords. This can be helpful in cases when a user has set a password for an account based on commonly available information or phrases in the username. Running this mode on many password files simultaneously may sometimes get more passwords cracked than it would if you ran it on the individual password files separately.
- Word List mode : This mode works through a specified wordlist like a password specified by the user for example seclist (https://github.com/danielmiessler/SecLists) which contains a bunch of categorized word lists. The application comes with a set of default wordlists.
- Incremental Mode : It is the most powerful cracking tool But it takes a large amount of time because it has a large amount of combinations. In order to crack a password it need the length of the password and its character set.
- External Mode : A cryptanalyst can define his/her own mode and use it by integrating with the John The Ripper.
Usage
a) Hash cracking
In order to demonstrate how we can crack a hashed value we will use Cyberchef to hash a value “hello” with the algorithm MD5.
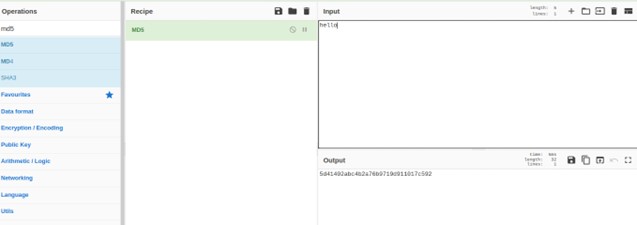
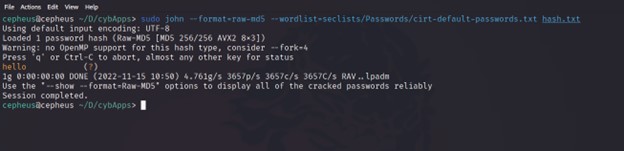
Then next we will copy the hash value into a text file called hash.txt and start cracking with the John The Ripper with the following command.
$ sudo john --format=raw-md5 --wordlist=seclists/Passwords/cirt-default-passwords.txt hash.txt
By changing the format parameter we can crack a lot of hashes. Since they contain and crack a lot of hashes and formats.
b) Compressed file cracking
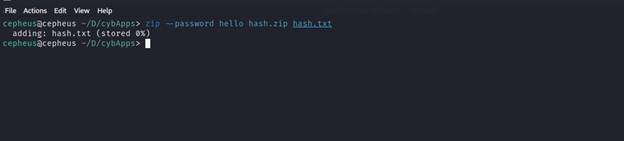
To start with this demonstration the first step is going to be preparing a password locked zip file with the command shown below.
>>> zip – password hello hash.zip hash.txt
This common will compress the file called hash.txt to hash.zip and secure it with the password hello
Let's assume we don’t have any idea about a security passcode to decompress the file hash.zip. The second step is going to be to extract the hash value the file contains and save it to a file called hash1.txt with the command below.
>>> zip2john hash.zip > hash1.txt
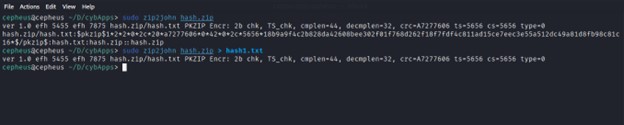
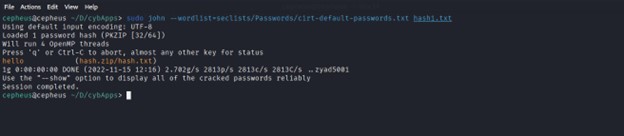
Then we will crack the hash value with John the ripper extracted from the zip file and successfully acquire the right code by auto detecting the hash algorithm and comparing the hashed value in the wordlists to the hash value in the file hash1.txt .
Conclusion
John The Ripper is an open source and very efficient password cracker by Open-Wall. It was originally built for Unix but is now available for fifteen different platforms including Windows, DOS, BeOS, OpenVMS and Unix-like operating systems. This tool has an updated version called Jumbo.
It is designed to be both feature-rich and fast. It combines several cracking modes in one program and is fully configurable for your particular needs. It is also available for several kinds of platforms and it is built with several hashing algorithms. It also auto detects the encryption on the hashed data and compares it against a large plain-text file that contains popular passwords.

