In this article, we will look into an open source phishing framework called Gophish. It is basically a cross platform simulating phishing framework that makes simulation of authentic phishing attempts very easy and efficient. From start to finish, you’ll be able to create realistic phishing simulations tailored to your organization. It is also very easy to install using a single click and get it up and running in just few seconds.
What is Phishing
Phishing is a type of cybercrime where a target or number of targets are contacted via email, phone call, or text message by someone posing as a legitimate organization in order to trick people into disclosing sensitive information like passwords, banking and credit card information, and personally identifiable information. Therefore GoPhish provides a well documented framework that makes this process more simple.
Important Features
- It is powered by a REST API.
- It has excellent web interface with rich set of options.
- It updates results in real time.
- Easy to Setup
- Easy to Use
- Gives Powerful results which looks like a magic.
![GoPhish: Open Source Phishing Framework [Ethical Hacking]](https://www.socialyzehub.com/wp-content/uploads/2023/01/gophish_open.jpg)
GoPhish: Open Source Phishing Framework [Ethical Hacking]
Also Read: Shellter: Dynamic Shellcode Injection Tool [Ethical Hacking]
First we need to install GoPhish by downloading it from https://getgophish.com/. It will download a zip file in your local system. You need to use unzip utility to uncompress the file. It will get uncompressed in a directory called gophish.
NOTE:
After uncompressing, switch to gophish directory and run sudo ./gophish command as shown below.
$ sudo chmod +x gophish
$ sudo ./gophish
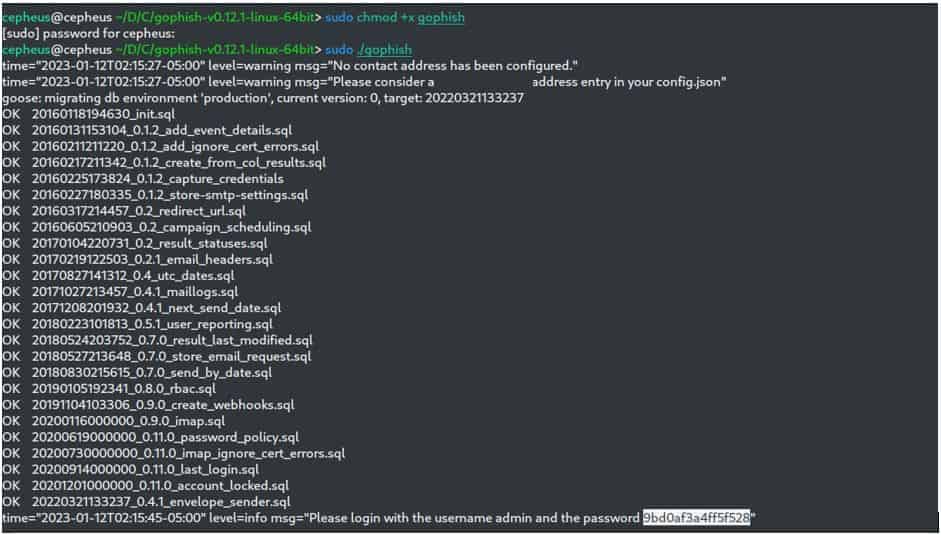
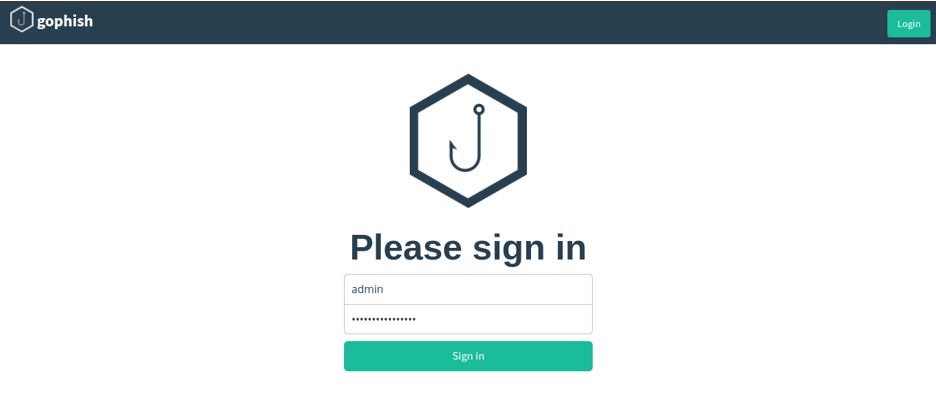
After entering above commands, GoPhish will automatically start the server and provide us with a username called “admin” and password generated as shown above on the output. Then we need to open a browser and enter the ip address configured in the config.json file or we can simply put the local server IP address i.e https://<IP_Address>:3333 in the browser. It should open the Sign In page as shown below.
NOTE:
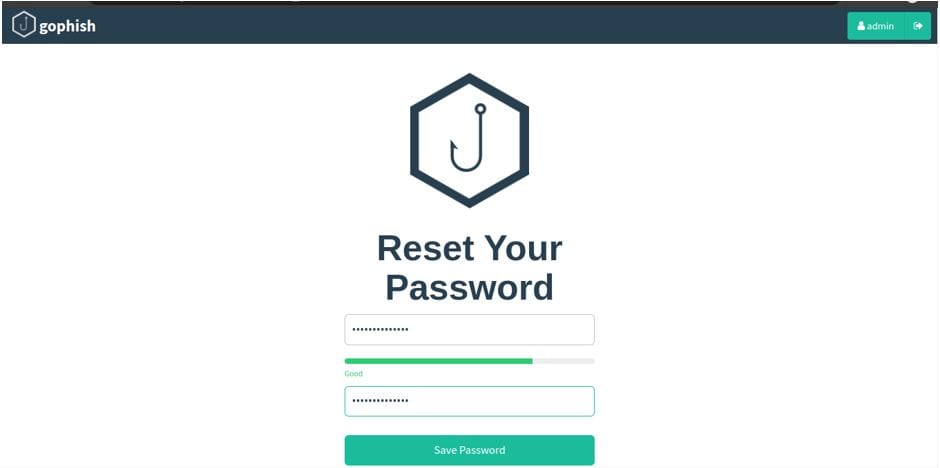
After logging in with the credentials provided by GoPhish, it will ask to reset the password as shown below. Once the new password is provided, click on Save Password to proceed.
Working Demonstration
Here we will see the working of GoPhish with help of simple demonstrations. Through demo, we will try to understand how to construct a sender's profile, how to create a landing page, how to create a template, how to deal with users and groups and finally how to start and proceed with phishing campaigns.
Sender’s Profile
To start with the demonstration, we need to first construct the sender's profile from Dashboard. The Sender’s profile is where we set up the profile for the sender’s information. In the sender profile, we need to fill some basic information like the sender’s name, the Sender’s Email address(it could be an organization’s or just individual’s address) and finally the SMTP server information. For this example, we will use gmail SMTP server along with our legitimate email and password.
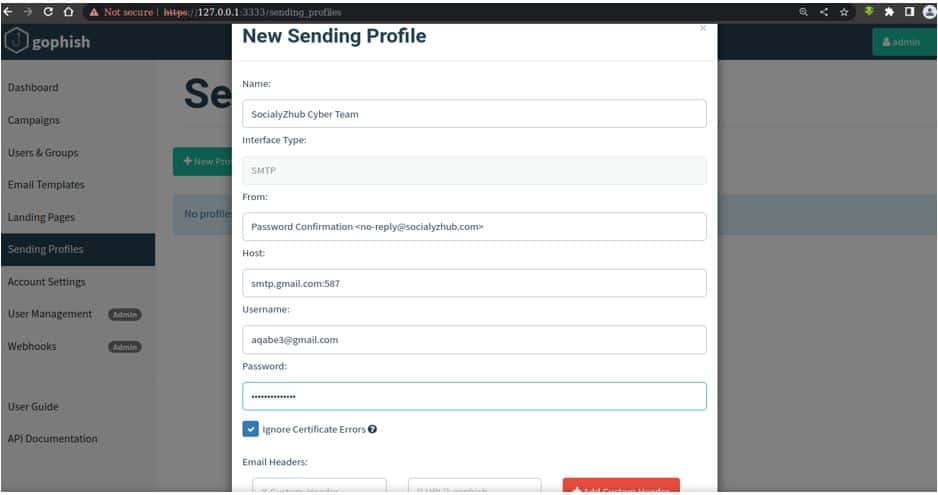
After filling above details, we can test it by clicking on “Send test Email”.
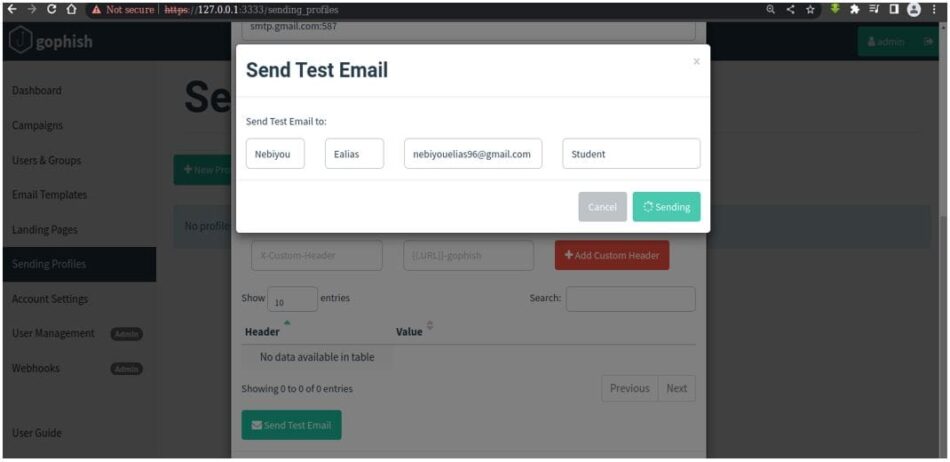
You need to also fill the receiver's details as shown above. And then simply hit send.
Landing Pages
Landing pages are the actual HTML pages that are returned to the users when they click the phishing links they receive. To create the landing page we have two ways - the first one is to craft the page manually and the second is to import any kind of site which could be malicious or any kind of HTML that have form submitted by the user.
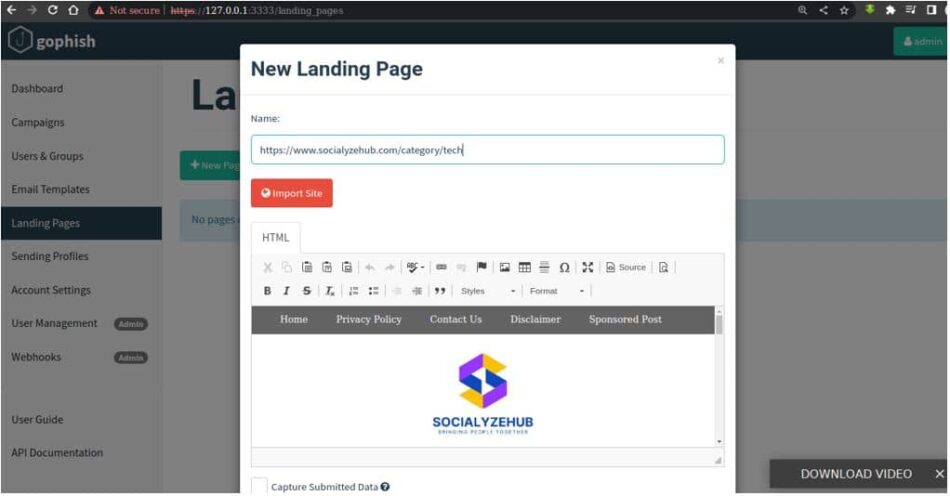
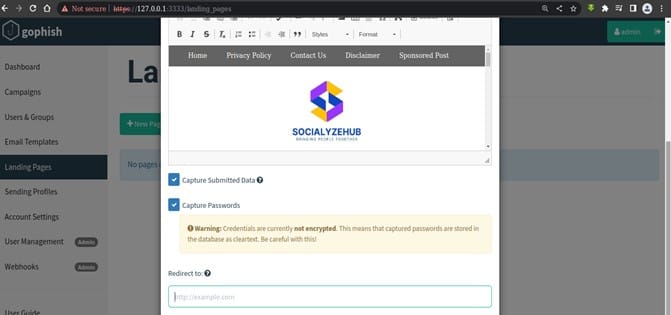
Landing pages support templating, capturing credentials, and redirecting users to another website after they submit their credentials. The Landing pages also enables the campaign admin to capture request especially password. We can simply do that by clicking on the option “capture submitted data” and “capture password”.
In the below options, we can see a text box that says “Redirects to”. In this text box we will enter the legitimate website link. After receiving the credentials we have to redirect the user to this original site so that user will not suspect that he/she was filling the form of a malicious site.
Template
Next is the template. To create a template, first we will navigate to email template and then start building from there. To create our template we can either use text format or HTML format. We can also import an email in a raw format.
For this demonstration we will import a sample email. To do that, we need to go to the email that we want to reproduce. You will see an option called Show original after clicking on three dots as shown below. Click on that option to show the original message.
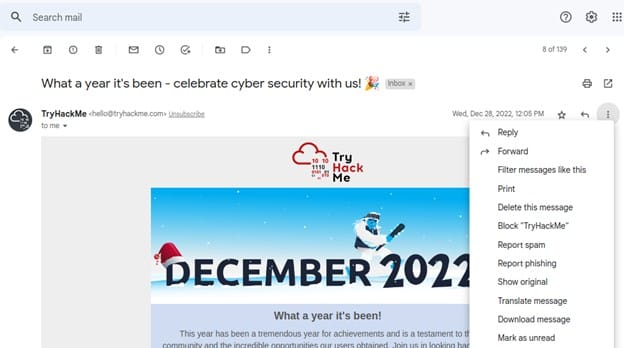
It should open like below. After being redirected to the original raw format, we need to copy it by simply clicking on “Copy to clipboard” as shown below.
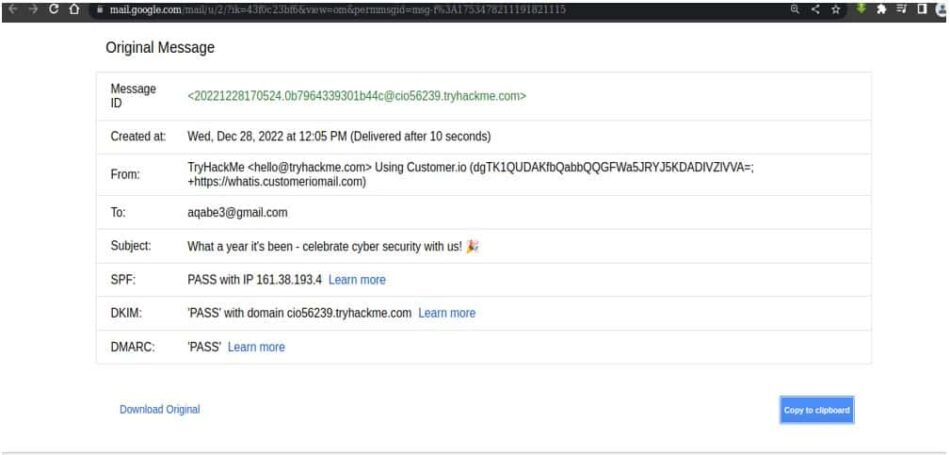
Then we need to paste it to our GoPhish email template where we will see the whole package. The advantage here is that we can customize the page as we would like so that we can inject payload, craft malicious web links etc.
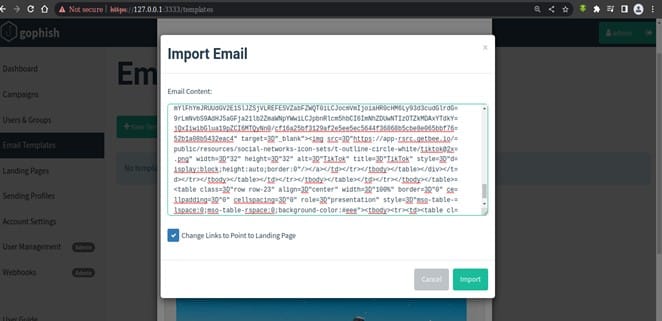
After copying the template, we need to click on import. The best part of this functionality is that we can import different files format such as pdf, compressed, image type etc. These types of files can be easily injected with the malicious code.
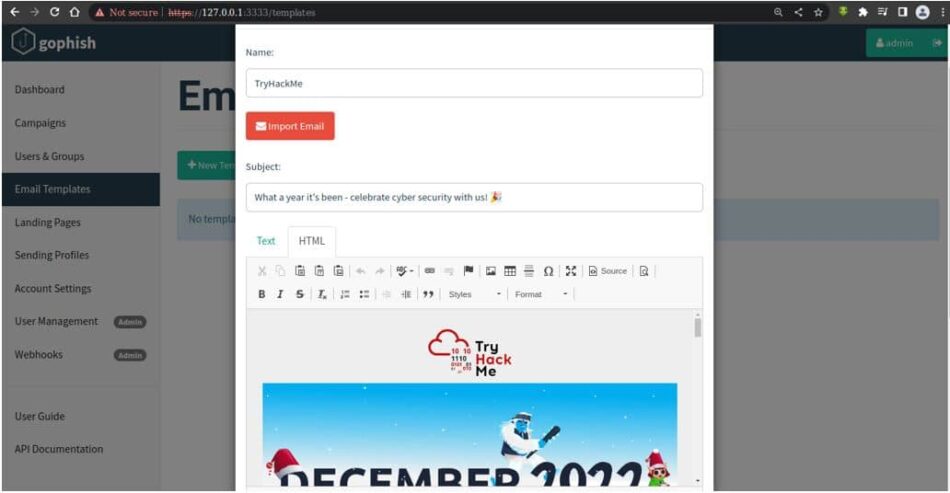
Users and Groups
Let’s say we would like to attack the whole organization with a Phishing attack. It would be very hard to send a Phishing email to everyone one by one. GoPhish has provided us the functionality where we can set numerous information about the Email address of Employees and send the crafted email once and send it using just a click.
We can also import Employee’s Information from an excel sheet which would even be a lot easier. After entering the Information, we just need to click on “Save Changes” as shown below.
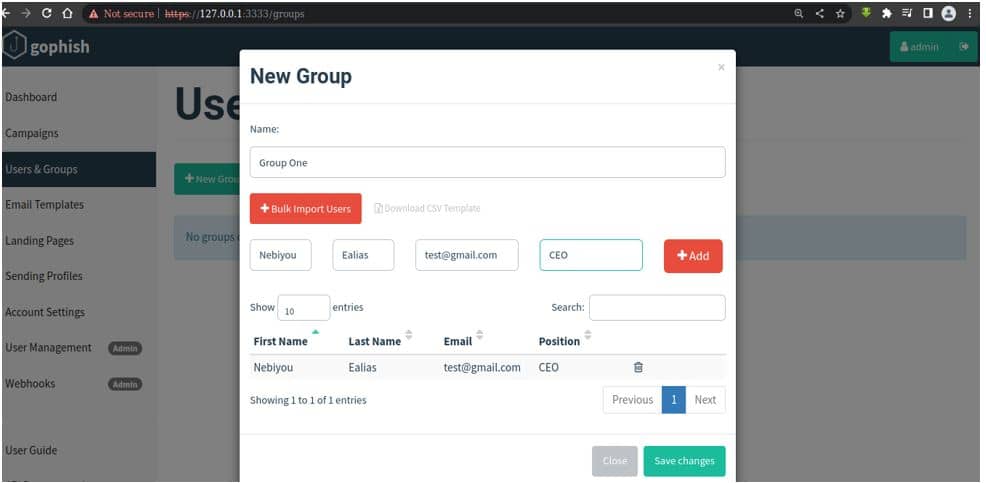
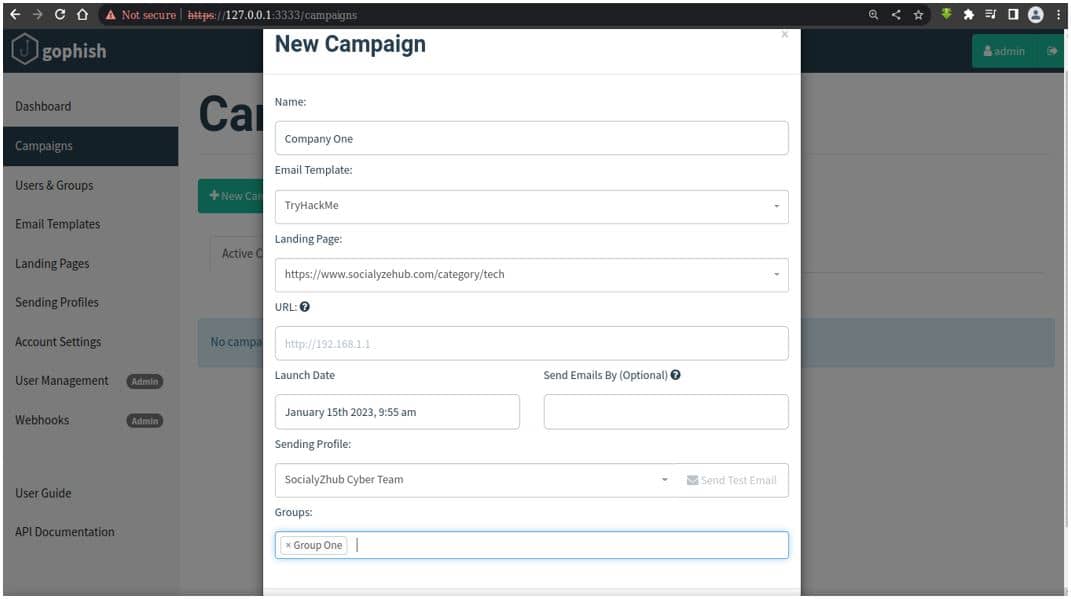
Create Campaign
This feature helps us Organize the Phishing Campaign and Launch It. In this feature we have to choose the Email Template, Landing Page, Set Date and Sender’s profile like the below image shows. After Selecting those parameters, we need to just click on “Launch Campaign”
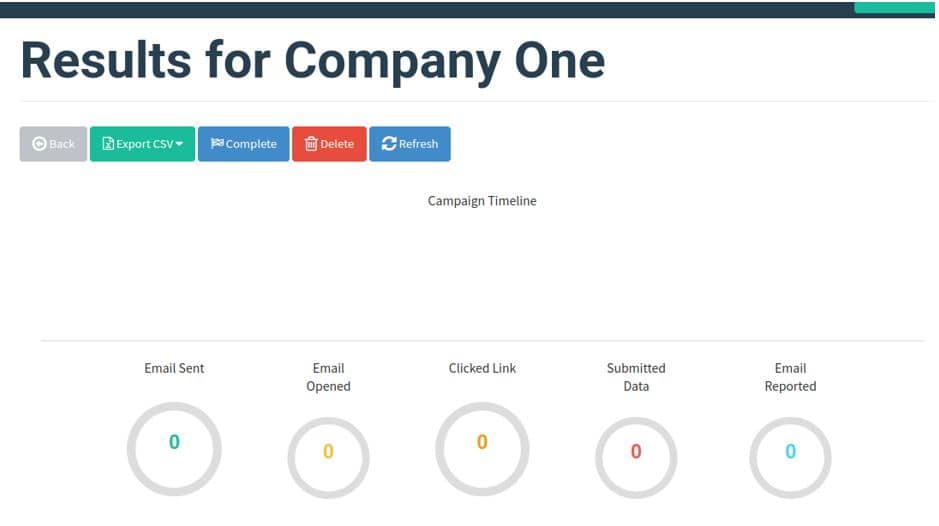
After sending the email, we will see a Result Graph that shows General Information about the Campaign such as email sent, email opened, clicked link, submitted data and email reported.
Conclusion
You can introduce interactive and educational cyber security awareness into your company through phishing simulation. Real-time phishing simulations are a quick and efficient technique to inform people and raise phishing attack awareness levels. GoPhish is one of the most well known Phishing Campaign software. This tool simplifies the process and execution of phishing Campaign by using different features like Group creation. It is a powerful, open-source phishing framework that makes it easy to test your organization's exposure to phishing.
