In the series of ethical hacking tutorial, today we are going to look into two Wifi hacking tools - Airgeddon and Wifi Honeypot. Both of the tools are free and open source and are extensively used for testing the security of any Wireless networks. So any company or organization who would like to check the vulnerability and password loopholes in their wireless networks would mostly use this tool because of the wide range of features it provides. We will discuss both of them in great detail here.
Airgeddon
Airgeddon is a Bash powered multi-use Wireless Security Auditing Script for Linux systems with an extremely extensive feature list.
Features
Airgeddon comes with many in-built features. Some of them are :-
- Full support for 2.4Ghz and 5Ghz bands
- Assisted WPA/WPA2 personal networks Handshake file and PMKID capturing
- Interface mode switcher (Monitor-Managed)
- Offline password decrypting on WPA/WPA2 captured files for personal networks (Handshakes and PMKIDs) using a dictionary, brute force and rule-based attacks with Aircrack, Crunch and Hashcat tools. Enterprise networks captured password decrypting based on John the Ripper, Crunch, Asleap and Hashcat tools.
- Evil Twin attacks (Rogue AP)
- WPS features
NOTE:
Installation
To install Airgeddon the first step is to clone the source code from GitHub using below command:-
$ git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git
The next step is to install Airgeddon using below command:-
$ cd airgeddon
$ sudo bash airgeddon.sh
Above command will install and then launch Airgeddon as shown below.
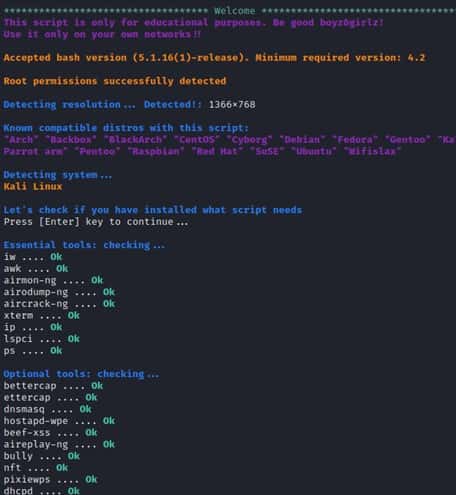
While opening the tool it will first check for all dependencies and necessary tools before launching this framework. It will attempt to install the essential tools if they are missing, which may take some time. As indicated in the picture once the installation is complete, you will see the OK status for both required and optional tools.
Usage
Airgeddon can be used for a lot of wireless security testing purposes and features. Some of them are:-
- Using Airgeddon we can switch interface mode. From Managed to Monitor and vice versa. We change to monitor mode because it enables us to see network traffic.
- It can capture a clean and optimized file , specifically a packet very simply. It also
- Can execute a DOS (Denial of service attack) attack over a network.
- Offline password cracking with both dictionary and rule based attacks with tools like Hashcat, Crunch and etc.
- Simple integrated sniffing (Hostapd DHCP DoS Ettercap).
- Integrated Sniffing, sslstrip (Hostapd DHCP DoS Ettercap Sslstrip).
- Integrated Sniffing, sslstrip2 and BeEF browser exploitation framework (Hostapd DHCP DoS + Bettercap + BeEF).
- Captive portal with “DNS blackhole” to capture Wifi passwords (Hostapd DHCP DoS Dnsspoff Lighttpd).
- Pixie dust attack
- Offline pin generation , brute force or known pin attack.
- Easy target Selection.
- Evil Twin attacks.
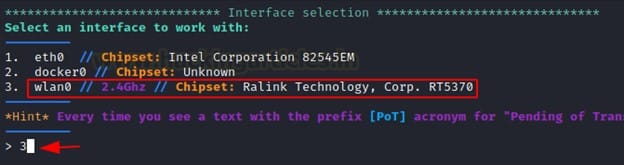
After the Installation process is finished we then will select our Network interface where Airgeddon will be working. We can choose our wifi card by selecting option number 3 as shown below.
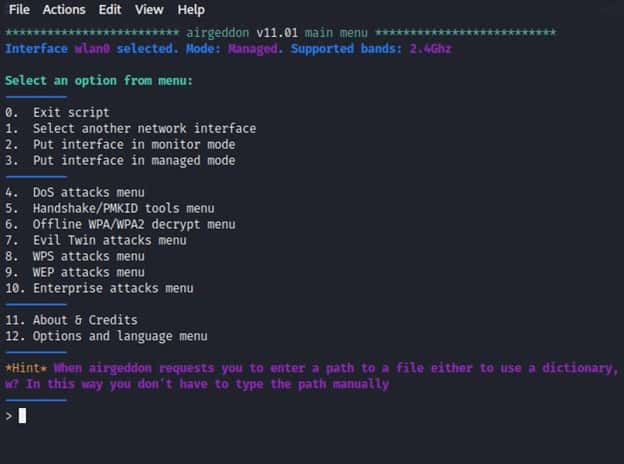
After selecting our network card we will have different alternatives to choose from to perform different tasks like change interface, select an attack type like DoS or Evil Twin attack.
Deauthentication Attack
Deauth attack is a Denial of Service which results in disconnection of a user and its wireless access point. The key motivation on why an attacker will perform a deauthentication attack is to force the client to perform an authentication back to the network and intercept the communication mainly to steal an information like password.
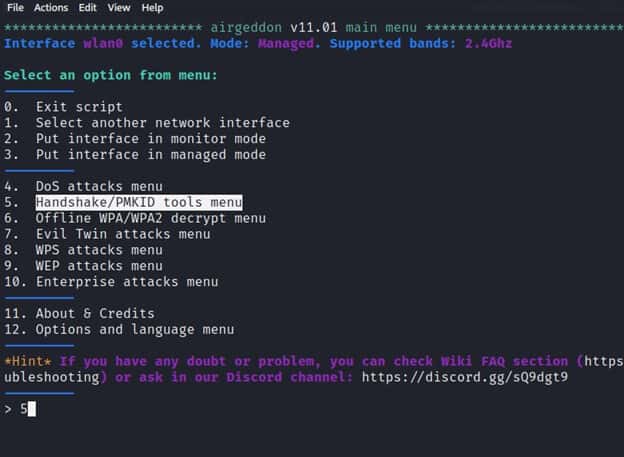
In order to execute a Deauth attack using Airgeddon we will change our interface to monitor mode by choosing the Option no 2 and then choose “Handshake /PMKID tools menu” which is option no 5 and hit Enter.
After selecting the Handshake and PMKID tools menu we will see options that enable to capture a handshake and PMKID.
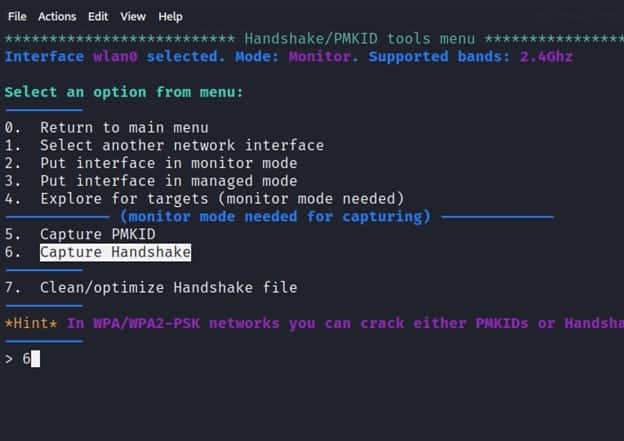
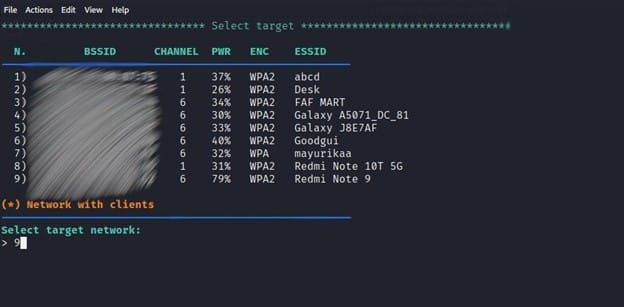
When you select option 6, a new window will appear, scanning for WPA and WPA2 networks and attempting to capture the 4-way handshake in a.cap file. After getting Target’s AP (Access Point), you can press CTRL+C
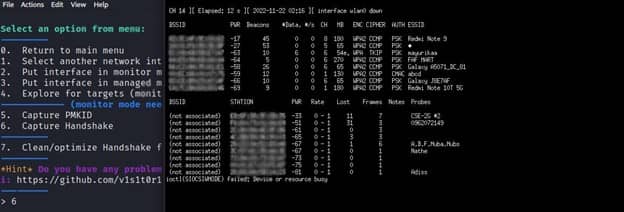
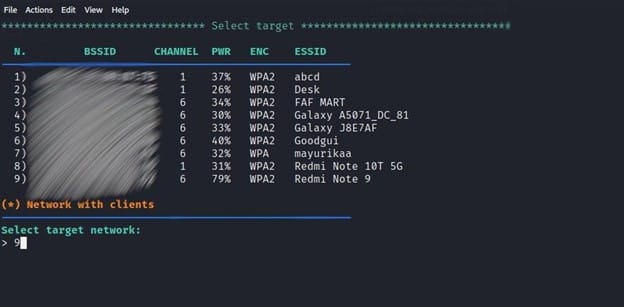
It will display a list of all ESSIDs (Wi-Fi names) examined, as well as their BSSID (MAC Address) and ENC encryption protocol type. Then, as we did for ESSID “Redmi Note 9”, you can pick your target by supplying a Serial Number.
Then we finally will launch our Deauth attack by sending a disassociation packet to the victim that is associated with a particular access point. We send this packet for several reasons:-
- Recovering a hidden ESSID. This is an ESSID that is not being broadcast. Another term for this is “cloaked”.
- Capturing WPA/WPA2 handshakes by forcing clients to reauthenticate
- Generate ARP requests (Windows clients sometimes flush their ARP cache when disconnected)
The next step is to select one of the disassoc attacks for this demonstration we will choose option number 2 which is “deauth aireplay attack” and we input a value for timeout.
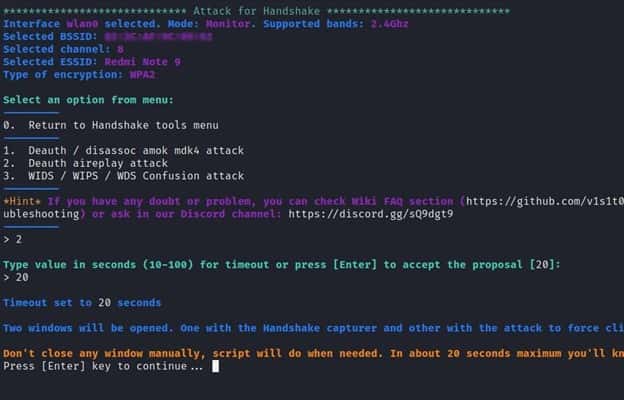
Now we will see that two windows appear. After deauthentication, one will attempt to undertake a deauth attack, while the other will attempt to record the 4 Way handshake between the client and the access point.
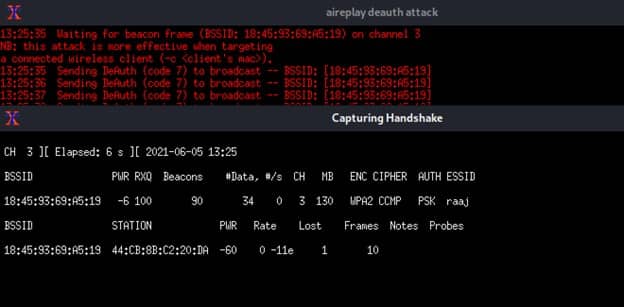
The above images shows the process of executing Deauth while capturing a handshake that can be used for different purposes.
Wifi HoneyPot
WiFi honeypots or hotspot honeypot are malicious honeypots which have the characteristics of a legitimate WiFi access point with an intention to steal information which is of interest to the attacker. Hackers use these WiFi honeypots to steal information such as Credit card information, Passwords and Login details. For this process we have selected Evil Twin attack.
Evil Twin attack : An evil twin attack takes place when an attacker sets up a fake Wi-Fi access point hoping that users will connect to it instead of a legitimate one. When users connect to this access point, all the data they share with the network passes through a server controlled by the attacker. Therefore to execute this attack first we will set our network interface to wlan0
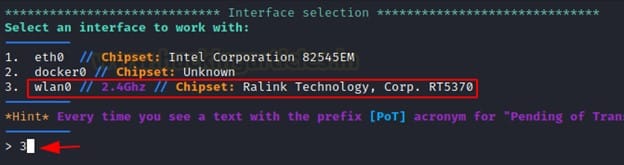
After choosing our network card we will change our mode to monitor and so we can execute the attack and select the attack method by entering option number 7 which is “Evil Twin”.
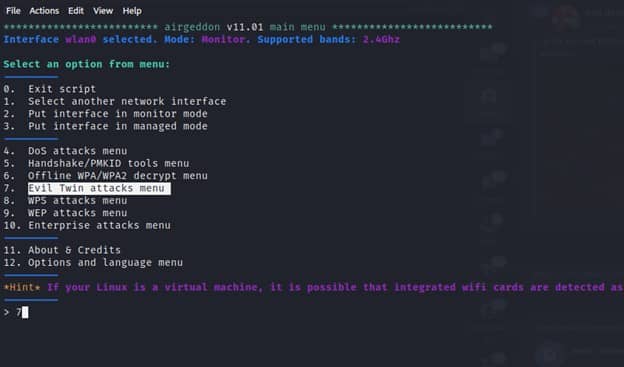
After selecting the Evil Twin attack menu we will see multiple menus that we can select from. The next step is to select a target by entering option number 4.
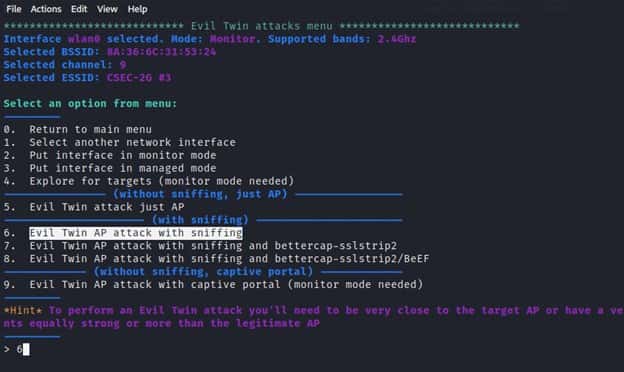
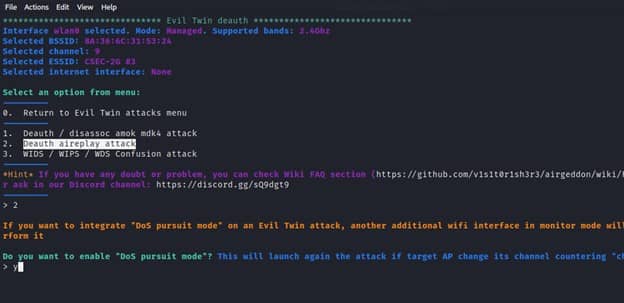
On Evil Twin attack sub menu, we have to specify the kind of the attack that we need to launch. In our case we need to sniff the passwords of victims who connect to the WiFi honeypot hence we will choose option number 6 for Evil Twin AP attack with sniffing and click enter.
Before launching an access point Wifi honeypot, we need to perform a deauthentication attack . This will cause the devices connected to the legitimate access point to disconnect hence they will reconnect on the Wifi honeypot. After we select the Deauth option we will be prompted to enable DOS pursuit mode. This mode allows you to keep on checking the target AP in case the channel changes during the attack.
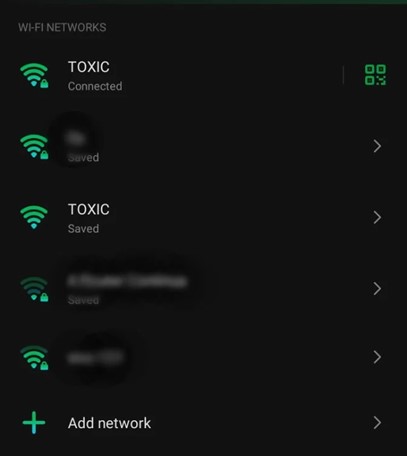
The next step will be to select another interface which will allow users to continue the connection. On the victim’s device shown below, we can see two access points bearing the same ESSID. The one which has a lock symbol is the legitimate one while the other one is the Wifi honeypot.
Once the victim connects to the honeypot, we can have access to his/her different sniffed information, especially the passwords.
Conclusion
Airgeddon is a multipurpose wireless hacking and penetration testing tool. It contains and integrates a very large number of tools in order to automate the whole hacking process. This tool is very easy and simple to use as well as effective since it consists of many kinds of features like changing interface mode and capturing a handshake.